Creating Custom Roles
The Calibo Accelerate platform provides 13 system-defined roles with permissions to perform specific tasks within the platform. Additionally, you can create custom roles with specific privileges based on your requirement. You can then assign custom roles to users or teams within the platform.
Before you create custom roles, you may want to understand the System-Defined Roles and Associated Permissions in the Calibo Accelerate platform.
Required Access
To view, create, edit, or delete a custom role in the Calibo Accelerate platform, you must have one of the following roles.
| Role | Description |
|---|---|
| Tenant Administrator |
This is the highest-level administrator with access to all the areas of the platform and is responsible for platform-wide configurations, settings, access management, and monitoring of all platform operations. |
| Configuration Administrator | A Configuration Administrator can manage various settings and configurations across the platform, which includes managing roles. |
| Custom role created for role management | A Tenant Administrator or Configuration Administrator can create a custom role specifically for role management. This role must have permissions to view, create, edit and delete roles. |
Creating a Custom Role
-
Sign in to the Calibo Accelerate platform and click Configuration in the left navigation pane.
- On the Platform Setup screen, on the Users, Roles, Teams, & Organization Hierarchy tile, click Manage.
- On the Roles tab, in the upper right corner, click + New Role, and do the following:
 Basic Details
Basic DetailsIn the Basic Details section, do the following:
Role Type
Select the desired role type. Depending on the type you choose, you can enable distinct levels of access and control for various roles as required.Role Type Scope Platform With platform roles, users can perform actions at the platform level. This includes managing global configurations, such as global settings on the Platform Setup screen or connection details of tools integrated with the Calibo Accelerate platform, dashboard management, release train management, user administration, and organizational hierarchy management, among others.
Product With product roles, users can perform actions across the Define, Design, Develop, and Deploy phases of product development within the platform. These actions include managing business requirements, user feedback, user stories, design artifacts, technologies, source code repository branch templates, data pipelines, and several other tasks related to technology deployment.
For the example Tools Integration Administrator role, let us select the Platform role type because this role needs platform-wide access to configure the connection details of tools and technologies.
Role Name
Give a name to the role. Give a name that clearly identifies the purpose of the role or its function in the Calibo Accelerate platform.Description
Provide a description for the role you are creating. An ideal description clarifies the role's purpose, the specific tasks it is intended to perform, or the areas of the platform it can access.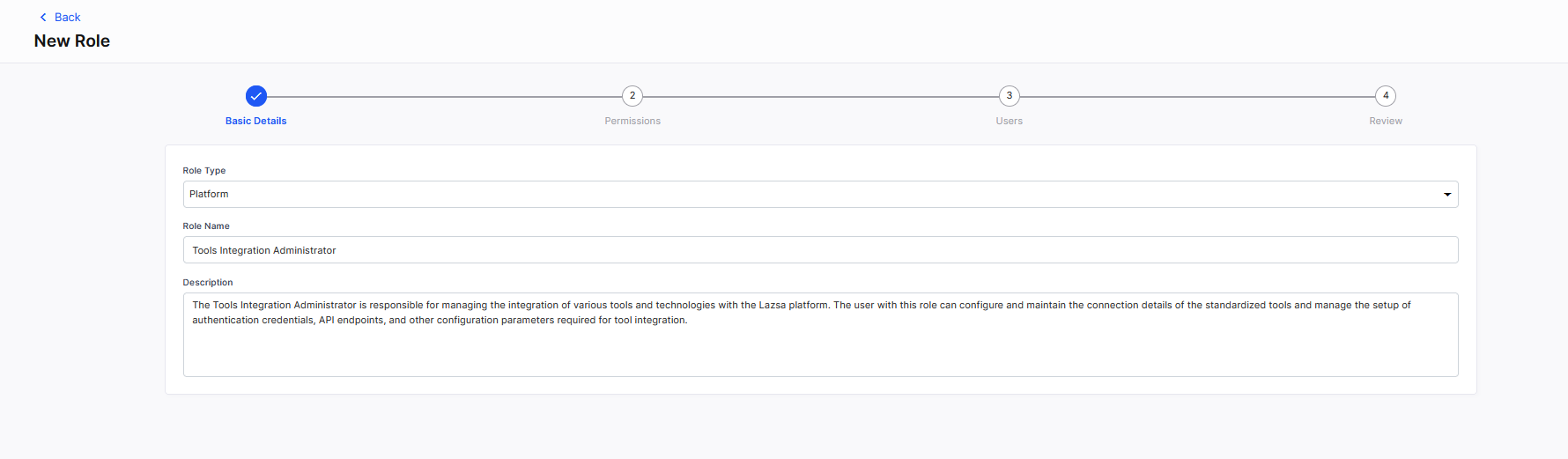
Click Next.
 Permissions
PermissionsPermissions are settings that control what users can see, access, and do within the Calibo Accelerate platform. In the Permissions section, each tab corresponds to a specific component or area within the Calibo Accelerate platform. Click each tab to view the corresponding permissions associated per component. To enable the permissions for the role that you are creating, turn on the toggle switch next to each desired permission. Depending on whether you create a platform role or a product role, the available permissions change.

Note:
You must enable at least one permission to proceed with role creation.

Note:
Dependent Permissions: Some permissions are interdependent. These dependency relationships might be within the same tab, or across different tabs in the Permissions section. Enabling a permission that other permissions depend on automatically enables all the dependent permissions. However, enabling a dependent permission does not automatically enable the permissions it depends on. For example, enabling the Configure/Edit Source Code Repository Tools permission automatically enables its dependent permission View Source Code Repository Tools Configuration. However, enabling the View Source Code Repository Tools Configuration permission does not automatically enable the Configure/Edit Source Code Repository Tools permission.
The following table contains the list of available permissions for each component of the platform depending on the role type.
 Platform Role Permissions
Platform Role PermissionsArea Component Available Permissions Dashboard Dashboard View Dashboard
Dashboard Admin
Product Portfolios Product Portfolios View Product Portfolios
Create Product Portfolios
Delete Product Portfolios
Products Products View Products
Create/Edit/Delete Products
Release Trains Release Trains View Release Trains
Create Release Trains
Delete Release Trains
Monitoring Monitoring Dashboard View Monitoring Dashboard
Maturity Assessment Maturity Assessment View Organization Maturity Assessment
Initiate Organization Maturity Assessment
View Maturity Assessment Recommendations
Manage Maturity Assessment Recommendations
View Maturity Assessment Action Plans
Manage Maturity Assessment Action Plans
Resource Planning Resource Planning View Resource Planning
Configuration Configuration View Configuration
Configuration Security & SSO View Security & SSO Configuration
Manage Security & SSO Configuration
Configuration Users View Users
Create/Edit Users
Delete Users
Configuration Roles View Roles
Create/Edit Roles
Delete Roles
Configuration Teams View Teams
Create/Edit Teams
Delete Teams
Configuration Organization Hierarchy View Organization Hierarchy
Add/Edit Organization Hierarchy
Delete Organization Hierarchy
Configuration Cloud Platforms View Configuration
Create/Edit Configuration
Delete Configuration
Configuration Technologies and Testing Tools View Technologies and Testing Tools Configuration
Select Technologies and Testing Tools
Configuration DevOps CI/CD Pipeline Configuration View DevOps Tools Configuration
Configure/Edit DevOps Tools
Delete DevOps Tools Configuration
Configuration Kubernetes Cluster Configuration View Kubernetes Cluster Configuration
Configure/Edit Kubernetes Cluster Connection Details
Delete Kubernetes Cluster Configuration
Configuration Terraform Configuration View Terraform Configuration
Configure/Edit Terraform Connection Details
Delete Terraform Configuration
Configuration Source Code Repository View Source Code Repository Tools Configuration
Configure/Edit Source Code Repository Tools Connection Details
Delete Source Code Repository Tools Configuration
Configuration Agile Planning Tools View Agile Tools Configuration
Configure/Edit Agile Tools Connection Details
Delete Agile Tools Configuration
Configuration Document Management Tools View Document Management Tools Configuration
Configure/Edit Document Management Tools Connection Details
Delete Document Management Tools Configuration
Configuration Databases and Data Warehouses View Databases and Data Warehouses Configuration
Configure/Edit Databases and Data Warehouses Connection Details
View Databases and Data Warehouses Configuration
Configuration Data Integration Tools View Data Integration Tools Configuration
Configure/Edit Data Integration Tools Connection Details
Delete Data Integration Tools Configuration
Configuration Data Visualization Tools View Data Visualization Tools Configuration
Configure/Edit Data Visualization Tools Connection Details
Delete Data Visualization Tools Configuration
Configuration Systems Integration View Systems Integration Tools Configuration
Configure/Edit Systems Integration Tools Connection Details
Delete Systems Integration Tools Configuration
Configuration Artifactory Management View Artifactory Management Tools Configuration
Configure/Edit Artifactory Management Tools Connection Details
Delete Artifactory Management Tools Configuration
Configuration Security Assessment View Security Assessment Tools Configuration
Configure/Edit Security Assessment Tools Configuration
Delete Security Assessment Tools Configuration
Configuration OpenShift Configuration View OpenShift Configuration
Configure/Edit OpenShift Connection Details
Delete OpenShift Configuration
Configuration Secret Management View Secret Management Tools Connection Details
Configure/Edit Secret Management Tools Connection Details
Delete Secret Management Tools Connection Details
Configuration General Settings View General Settings
Manage General Settings
Configuration Machine Configuration Settings View Machine Configuration Settings
Manage Machine Configuration Settings
Configuration Security Settings View Security Settings
Manage Security Settings
Configuration Themes Settings View Themes Settings
Manage Themes Settings
Configuration Audit Log Settings View Audit Log Settings
Manage Audit Log Settings
Configuration Terminology Settings View Terminology Settings
Manage Terminology Settings
Configuration Custom Field Settings View Custom Field Settings
Manage Custom Field Settings
Configuration Agile Project Settings View Agile Project Settings
Manage Agile Project Settings
Configuration Scheduler Settings View Scheduler Settings
Manage Scheduler Settings
Configuration Dropdown Field Settings View Field Values
Add/Edit Field Values
Configuration Cloud Tag Settings View Cloud Tag Settings
Manage Cloud Tag Settings
Configuration Audit Logs View Audit Logs
Configuration Account Info View Account Info
Manage Account Info
Configuration Data Crawler View Data Crawler
Create and Run Data Crawler
Rerun Data Crawler
Delete Data Crawler
Configuration Data Catalog View Data Catalog
Create Data Catalog
Delete Data Catalog
Import Data Catalog
Configuration Policy Template View Policy Template
Manage Policy Template
Configuration Branch Template View Branch Template
Manage Branch Template
Configuration Workflow Template View Workflow Template
Manage Workflow Template
Configuration Workflow Usage View Workflow Usage
Add/Edit Workflow Usage
Configuration Maturity Assessment View Maturity Assessment
Manage Maturity Assessment
Configuration Calibo Accelerate Orchestrator Agents View Calibo Accelerate Orchestrator Agents
Add/Edit Calibo Accelerate Orchestrator Agents
Delete Calibo Accelerate Orchestrator Agents
 Product Role Permissions
Product Role PermissionsArea Component Available Permissions Product Product View product
Edit Product
Delete Product
Initiate Product Maturity assessment
Initiate Team Maturity Assessment
Define Add/Edit User Feedback
Delete User Feedback
Convert User Feedback to Business Requirement
Add/Edit Business Requirement
Delete Business Requirement
Manage User Stories
Design Add/Edit Design
Delete Design
Develop Add Technologies
Delete Technologies
Manage Branch Template
Manage Branch Access
Data Pipeline Studio View Data Pipeline
Data Crawler View Data Crawler
Create and Run Data Crawler
Rerun Data Crawler
Delete Data Crawler
Data Catalog View Data Catalog
Create Data Catalog
Delete Data Catalog
Import Data Catalog
Develop Pipeline Create/Edit Pipeline
Delete Pipeline
Import Pipeline
Export Pipeline
Manage Pipeline Version
Manage Pipeline Run Timeout
Manage Pipeline Manage Pipeline Notification
Schedule Pipeline
Manage Pipeline Chain
Run/Terminate Pipeline
Promote Pipeline
Manage Wheel Package
DataOps View DataOps
Deploy Add/Edit Stage
Delete Stage
Add/Edit Technology
Deploy Technology
Uninstall Technology
Configure Instance
Configure Cluster
Manage Terraform Runs
Manage Jenkins Job Runs
Manage Secrets
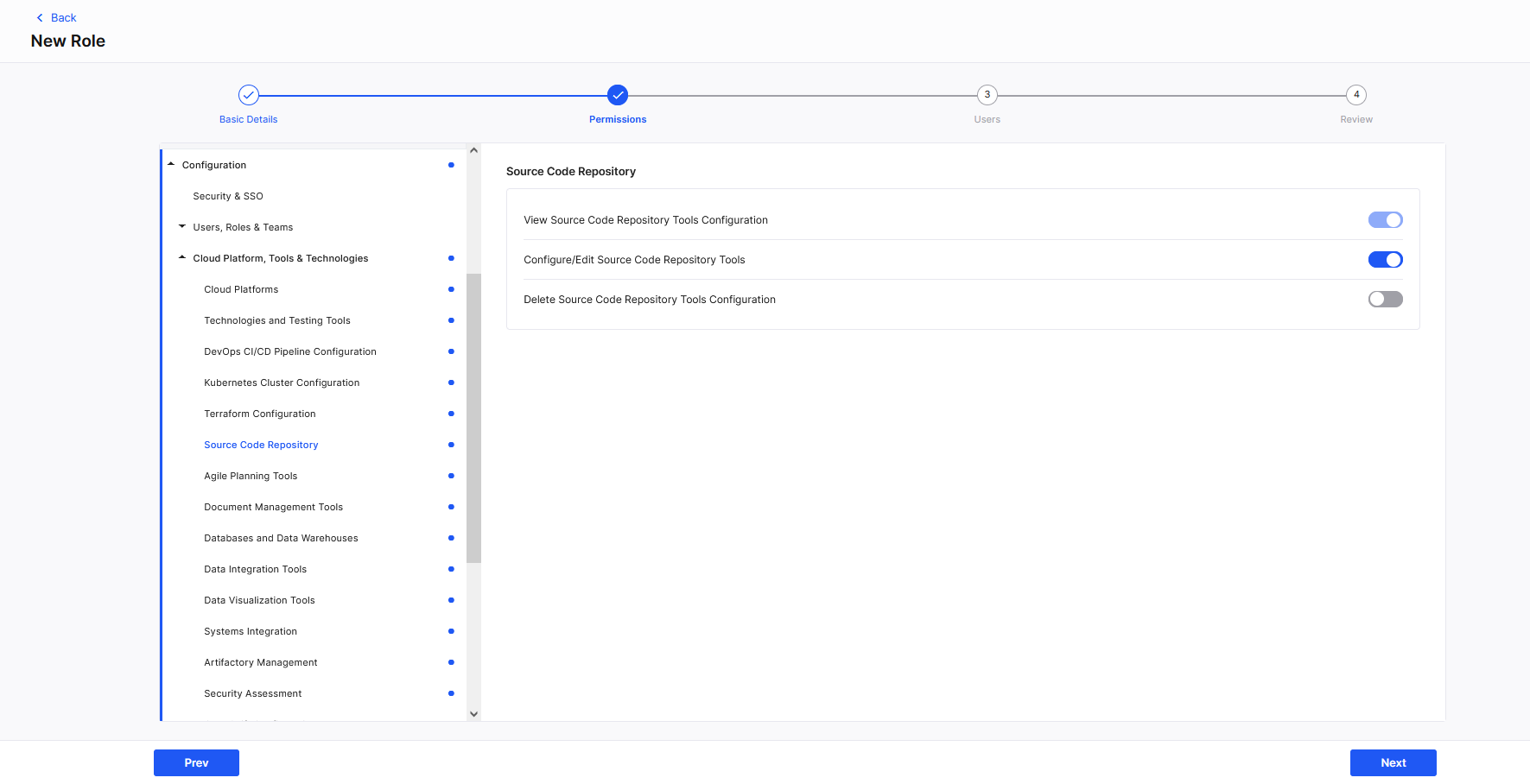
After you enable the desired permissions, click Next.
 Users
UsersThis section is visible if you are creating a Platform role.
In the Users section, assign the custom role to one or more users as per your requirement.
Use the search box to find the desired users and add them to the custom role. However, this step is optional at this point. You can proceed without assigning this custom role to anyone for now and complete the process later as needed.
Click Next to review your role definition or click Prev to return to the previous screen.
 Tools
Tools
Note:
Ensure that users who want to access the integrated tools from within the Calibo Accelerate platform are already added to the relevant tools before syncing their tool-specific roles and permissions from the Calibo Accelerate platform.
This section is visible if you are creating a Product role.
As an Administrator, on the Cloud Platforms, Tools & Technologies screen, you configure the connection details for various tools and technologies integrated with the Calibo Accelerate platform. In the Tools section, you can decide which tools your custom role can access, and the actions the role can perform on each tool.
When you assign a custom role to a user at a product level, the roles and permissions you specify in this section are assigned to the user for the tools associated with that product.
For details on how access control and permissions work for these tools, refer to the vendor documentation for each respective tool.
To assign tools-related permissions for your custom role, refer to the following sections for your desired tools.
 Jira
JiraEnable Access : To allow your custom role to access your configured Jira instance from the Calibo Accelerate platform, and to assign the required Jira roles to the custom role, turn on the toggle.
Roles: To assign the desired Jira roles to your custom role, do either of the following:
Enter the desired Jira role in the Roles box and press the Enter key. You can assign multiple Jira roles to a custom role in Calibo Accelerate.
Alternatively, click connect to a Jira instance and from the list of configured instances, choose the one from which you want to fetch the configured roles. Click Get Roles to retrieve all the roles configured in the selected Jira instance. Select the checkboxes for the desired roles and click Add Roles.
 Confluence
ConfluenceEnable Access : To allow your custom role to access your configured Confluence instance from the Calibo Accelerate platform, and to assign the required Confluence permissions to the custom role, turn on the toggle.
Space Permissions
Select the appropriate Confluence space permissions for your custom role. The following options are available.Category Permissions All View
Delete Own
Pages Add
Archive
Delete
Blog Add
Delete
Attachments Add
Delete
Comments Add
Delete
Restrictions Add
Delete
Space Export
Admin
Page Permissions
Can View
Can Edit
 Bitbucket
BitbucketEnable Access : To allow your custom role to access your configured Bitbucket instance from the Calibo Accelerate platform, and to assign the required Bitbucket permissions to the custom role, turn on the toggle.
Permissions
Select the appropriate Bitbucket Server project permissions and repository permissions for your custom role. The following options are available.Category Permissions Project Access Read
Write
Admin
Repo Access Read
Write
Admin
 Bitbucket Cloud
Bitbucket CloudEnable Access : To allow your custom role to access your configured Bitbucket Cloud instance from the Calibo Accelerate platform, and to assign the required Bitbucket Cloud permissions to the custom role, turn on the toggle.
Permissions
Select the appropriate Bitbucket Cloud project permissions and repository permissions for your custom role. The following options are available.Category Permissions Project Access Read
Write
Create
Admin
Repo Access Read
Write
Admin
 Jenkins
JenkinsEnable Access : To allow a custom role to access your configured Jenkins instance from the Calibo Accelerate platform, and to assign the required Jenkins permissions to the custom role, turn on the toggle.
Permissions
Select the appropriate Jenkins permissions for your custom role. The following options are available.Category Permissions Job Build
Delete
Create
Configure
Workspace
Cancel
Move
Discover
Read
View Delete
Configure
Create
Read
Credentials View
Update
Manage Domains
Create
Run Delete
Update
Replay
SCM Tag
 JFrog
JFrogEnable Access : To allow a custom role to access your configured JFrog instance from the Calibo Accelerate platform, and to assign the required JFrog permissions to the custom role, turn on the toggle.
Permissions
Select the appropriate JFrog permissions for your custom role. The following options are available.Category Permissions Repository Permissions Read
Annotate
Deploy/Cache
Delete
Manage XRay Metadata
Manage
 SonarQube
SonarQubeEnable Access : To allow a custom role to access your configured SonarQube instance from the Calibo Accelerate platform, and to assign the required SonarQube permissions to the custom role, turn on the toggle.
Permissions
Select the appropriate SonarQube permissions for your custom role. The following options are available.Administer
Administer Issues
Administer Security Hotspots
Browse
Execute Analysis
See Source Code
 Databricks
DatabricksEnable Access : To allow a custom role to access your configured Databricks instances from the Calibo Accelerate platform, and to assign the required Databricks permissions to the custom role, turn on the toggle.
Permissions
Select the appropriate Databricks permissions for your custom role. The following options are available.Databricks Instance - Select a Databricks instance for which you want to assign permissions to the custom role.
Assign cluster and workspace/folder level permissions to the custom role, using this option.
Cluster Access Permissions
Select one of the following cluster access permissions for your custom role:Can Manage
Can Restart
Can Attach To
Workspace/Folder Permissions
Select one of the following Databricks workspace or folder permissions for your custom role:Can Run
Can Manage
Can Read
Can Edit
Click Add.
 Snowflake
SnowflakeEnable Access : To allow your custom role to access your configured Snowflake instance from the Calibo Accelerate platform, and to assign the required Snowflake permissions to the custom role, turn on the toggle.
You can map an already configured role in your Snowflake account to your custom role or create a new role.
 Map existing role
Map existing roleTo map an existing Snowflake role to your custom role, do the following:
Snowflake Instance
Select the Snowflake instance on which you want to grant access to the custom role.Role
From the list of roles existing on the selected Snowflake account, select the desired role that you want to map.Object
Select the desired object from the list.Depending on the object you choose, the following options are available. Select the option required for your custom role.
Object Options WAREHOUSE - The list of available warehouses is displayed. Select the warehouse on which you want to grant access to the custom role.
- Review the list of privileges assigned to the selected Snowflake role on the selected warehouse and click Add.
SCHEMA - Select the database and the schema on which you want to grant privileges to the custom role.
- Review the privileges assigned to the selected Snowflake role on the selected database and schema and click Add.
DATABASE - Select the database on which you want to grant privileges to the custom role.
- Review the privileges assigned to the selected Snowflake role on the selected database and click Add.
TABLE - Select the database, schema, and the table on which you want to grant privileges to the custom role.
- Review the privileges assigned to the selected Snowflake role on the selected table and click Add.
 Create new role
Create new roleTo create a new role in Snowflake and map it to your custom role in the Calibo Accelerate platform, do the following:
Snowflake Instance
Select the Snowflake account on which you want to create a new role.Object
Select the desired object from the list.Depending on the object you choose, the following options are available. Select the option required for the new Snowflake role.
Object Options WAREHOUSE - The list of available warehouses is displayed. Select the warehouse on which you want to grant access to the custom role.
- For the selected warehouse, assign the desired privileges to the new Snowflake role.
SCHEMA - Select the database and the schema on which you want to grant privileges to the custom role.
- For the selected schema, assign the desired privileges to the new Snowflake role.
DATABASE - Select the database on which you want to grant privileges to the custom role.
- For the selected database, assign the desired privileges to the new Snowflake role.
TABLE - Select the database, schema, and the table on which you want to grant privileges to the custom role.
- For the selected table, assign the privileges to the new Snowflake role.
 GitHub Server
GitHub ServerEnable Access : To allow your custom role to access your configured GitHub Server instance from the Calibo Accelerate platform, and to assign the required GitHub Server role to the custom role, turn on the toggle.
Roles:
To assign the desired GitHub Server role to your custom role, do either of the following:Enter the desired GitHub Server role in the Roles box and press the Enter key.
Alternatively, click connect to a configuration and from the list of configured GitHub Server instances, choose the one to grant access to the role being created. Click Get Roles to retrieve all the roles configured in the selected GitHub Server instance. Choose the role that best fits your custom role and click Add Role.
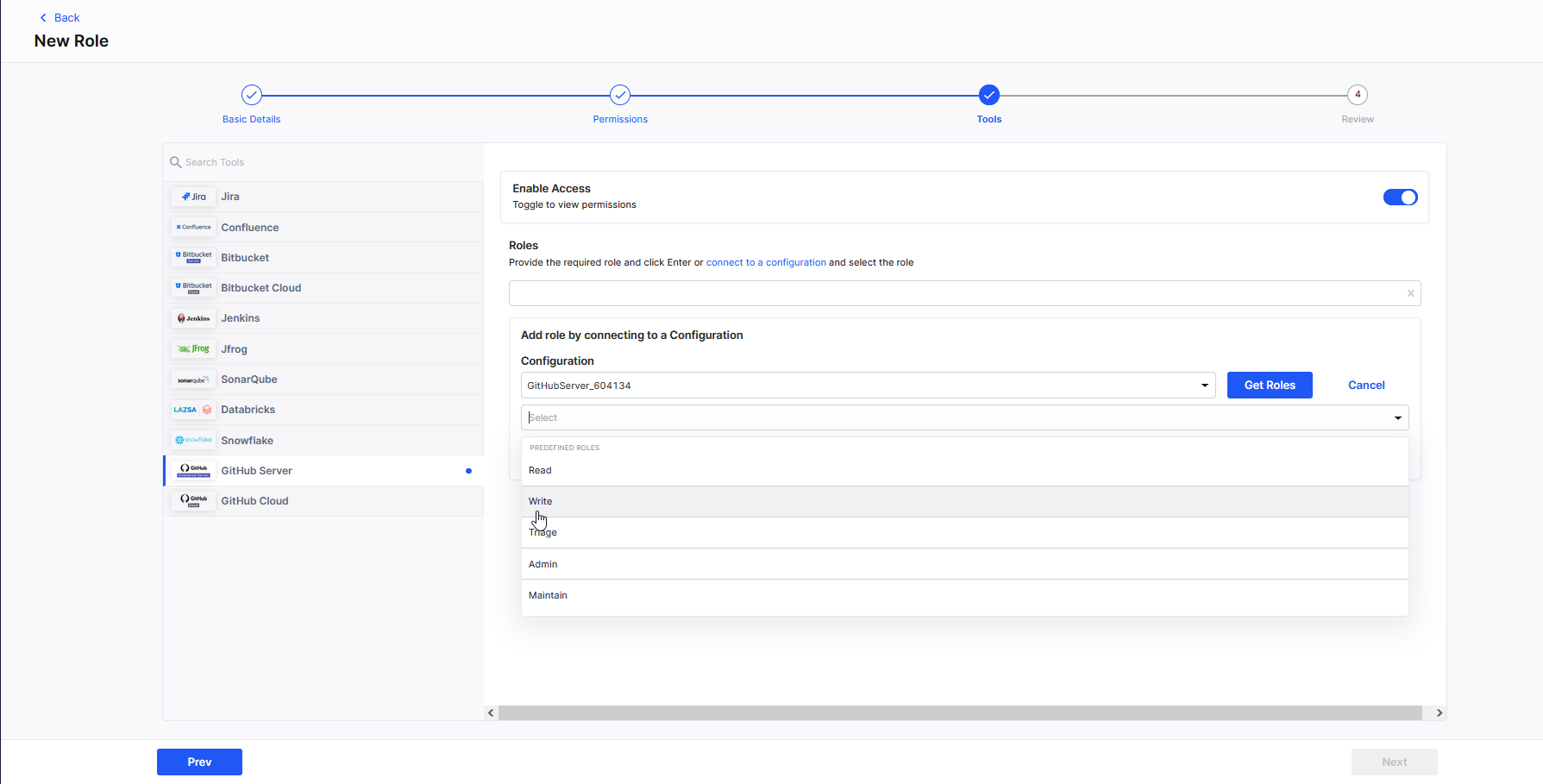
 GitHub Cloud
GitHub CloudEnable Access : To allow a custom role to access your configured GitHub Cloud instance from the Calibo Accelerate platform, and to assign the required GitHub Cloud permissions to the custom role, turn on the toggle.
Roles:
To assign the desired GitHub Cloud role to your custom role, do either of the following:Enter the desired GitHub Cloud role in the Roles box and press the Enter key.
Alternatively, click connect to a configuration and from the list of configured GitHub Cloud instances, choose the one to grant access to the role being created. Click Get Roles to retrieve all the roles configured in the selected GitHub Cloud instance. Choose the role that best fits your custom role and click Add Role.
 GitLab
GitLabEnable Access : To allow your custom role to access your configured GitLab instance from the Calibo Accelerate platform, and to assign the required GitLab permissions to the custom role, turn on the toggle.
Roles:
Select the desired GitLab role that you want to assign to your custom role. The following Project roles are available:
Guest
Reporter
Developer
Maintainer
Owner
A user assigned the Guest role has the least permissions, and the Owner has the most. For more information about permissions and roles in GitLab, refer to the GitLab documentation.
 Qlik Sense
Qlik SenseEnable Access : To allow your custom role to access your configured Qlik Sense instance from the Calibo Accelerate platform, and to assign the required Qlik Sense permissions to the custom role, turn on the toggle.
Permissions:
Qlik Sense Instance
From the list of configured Qlik Sense instances, select the instance on which you want to grant access to your custom role.Object
Select Space.Space
All the spaces created in the selected Qlik Sense instance are available in the dropdown list. You can select specific spaces or select all to grant access to your custom role.Permission
Select one or more of the following permissions on the selected Qlik Sense spaces for your custom role:Can consume data
Can edit
Can edit data in apps
Can manage
Can view
 Review
ReviewIn the Review section, you see the entire definition of your custom role, including basic details, granted permissions, and assigned users (for platform roles) or permitted tools (for product roles). Review all details carefully.
To make changes, click Prev.
Click Create Role to finalize your role definition.
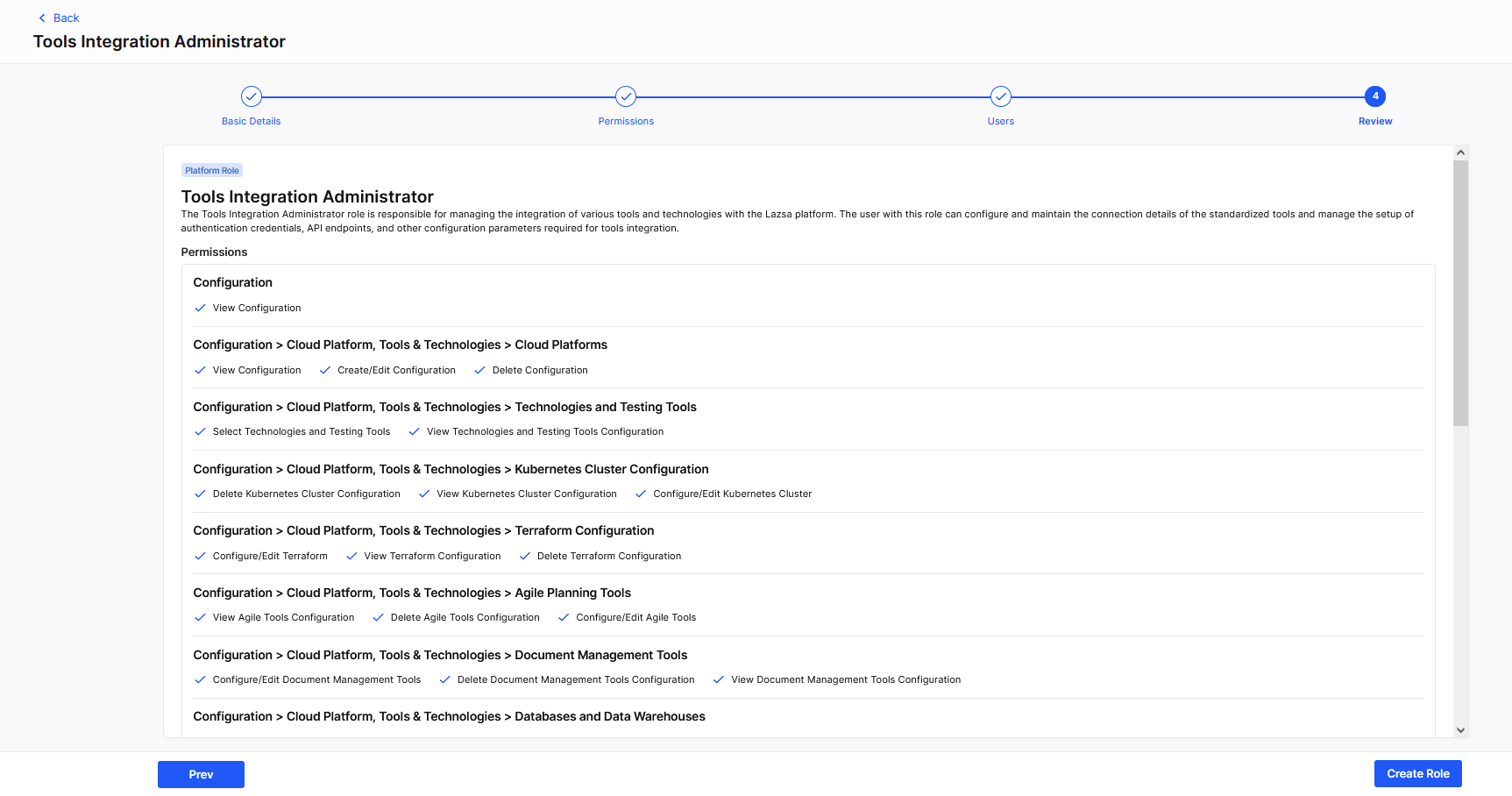
Thus, our example custom role Tools Integration Administrator is created.
You are done with creating custom roles as well as assigning them to users. You may now want to create teams.
| What's next? Create Teams |