Manage Secrets for Technology Deployments
Depending on the architecture, integration, and dependencies of your application, various kinds of secrets are required for the technology or the application to work fine. These secrets include database credentials, API keys, encryption keys, authentication tokens, certificates, and access tokens, among others. As a standard security practice, such secrets are stored in a secrets management tool like HashiCorp Vault or AWS Secrets Manager. When you deploy your application in the deployment workflow of the Calibo Accelerate platform, you can choose to inject these secrets at runtime, instead of hard-coding them directly into the application code or configuration files.
On the Manage Secrets tab of the deployment workflow within a stage, you can save the details related to the secrets that you want to dynamically inject at runtime. On the Deployment tab, when you add and deploy technologies on your Docker container or Kubernetes cluster, you can select a secret to be injected from the list of saved secrets, thereby avoiding exposure of credentials in your code or configuration.
Depending on your preferred deployment mode, refer to the following sections:
-
Managing Secrets for Technology Deployments on Kubernetes Cluster
-
Managing Secrets for Technology Deployments on Docker Container
Managing Secrets for Technology Deployments on Kubernetes Cluster
Managing secrets for Kubernetes deployments involves configuring the details of a secret on the Manage Secrets tab of a deployment workflow and enabling HashiCorp secret injection during technology deployment.
Prerequisites
Before you use the secret injection feature in the deployment workflow, make sure that you complete the following prerequisites on the Kubernetes cluster where you want to deploy technologies or applications.
-
Make sure your have HashiCorp Vault installed and configured. See Set Up HashiCorp Vault.
-
Make sure that your Vault integration with Kubernetes is working fine. See Inject Secrets into a Kubernetes Pod.
Configuring Secrets in Calibo Accelerate platform
-
Go to the stage in the deployment workflow of a product feature where you want to add and deploy technologies.
-
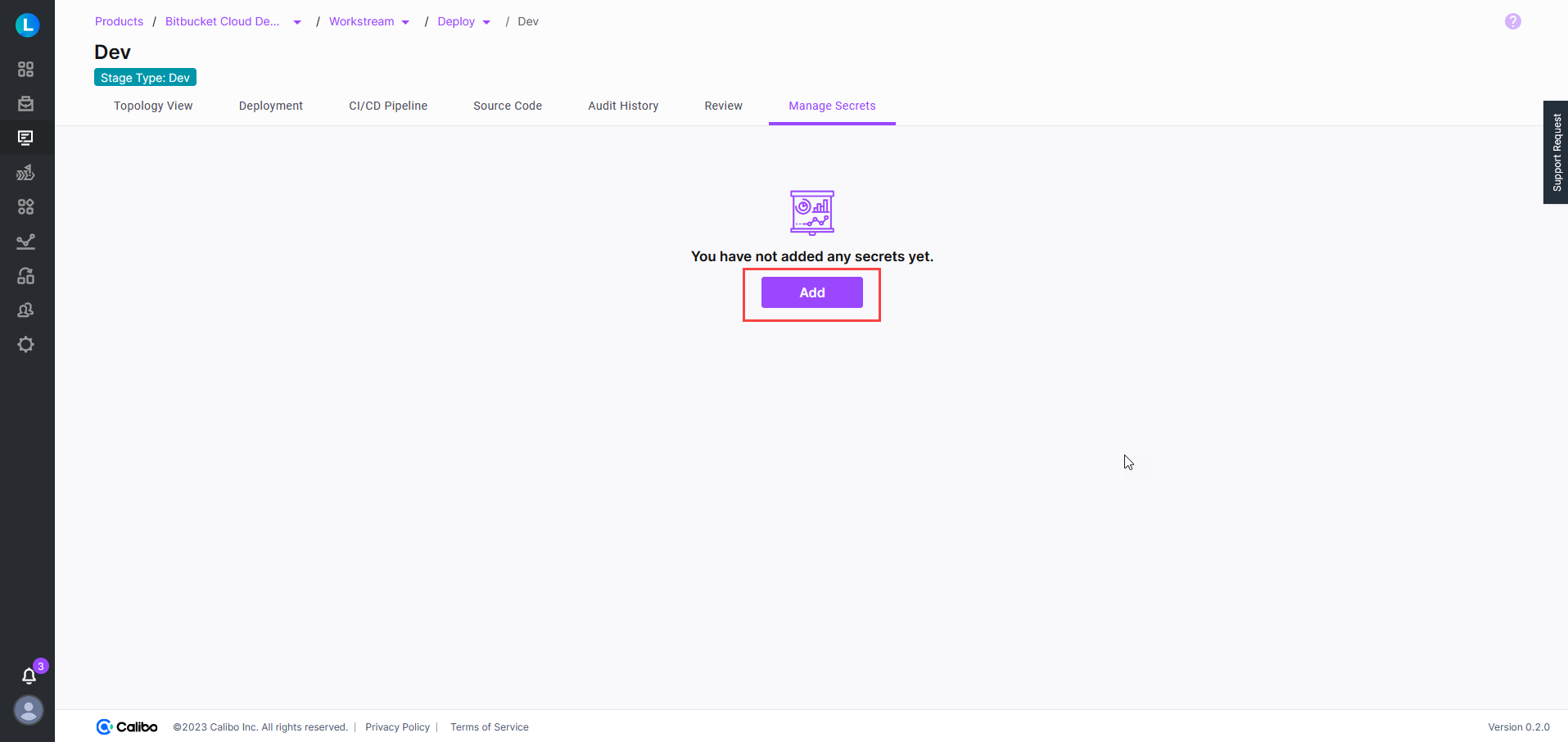
On the Manage Secrets tab, click Add to configure the details of your HashiCorp Vault secret.
-
In the Add Secret side drawer, enter the following details:
-
Secret Name: Provide the name of the secret stored in Vault.
-
Secret Management Tool: Select HashiCorp Vault.
-
Deployment Mode: Choose Kubernetes.
-
Path: Specify the path to the secret in HashiCorp Vault, for example,
/dev/apps/mysecrets.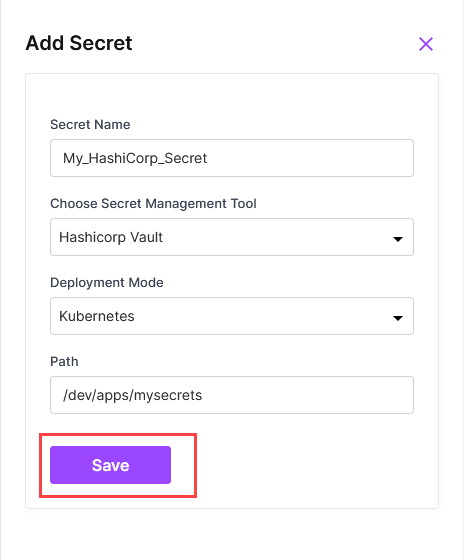
-
-
Save the configured details.
Your configured secret is listed and ready to be used during the deployment of your technology within the Calibo Accelerate platform. You can edit or delete it any time as required.
-
Go to the stage in the deployment workflow of a product feature where you want to add and deploy technologies.
-
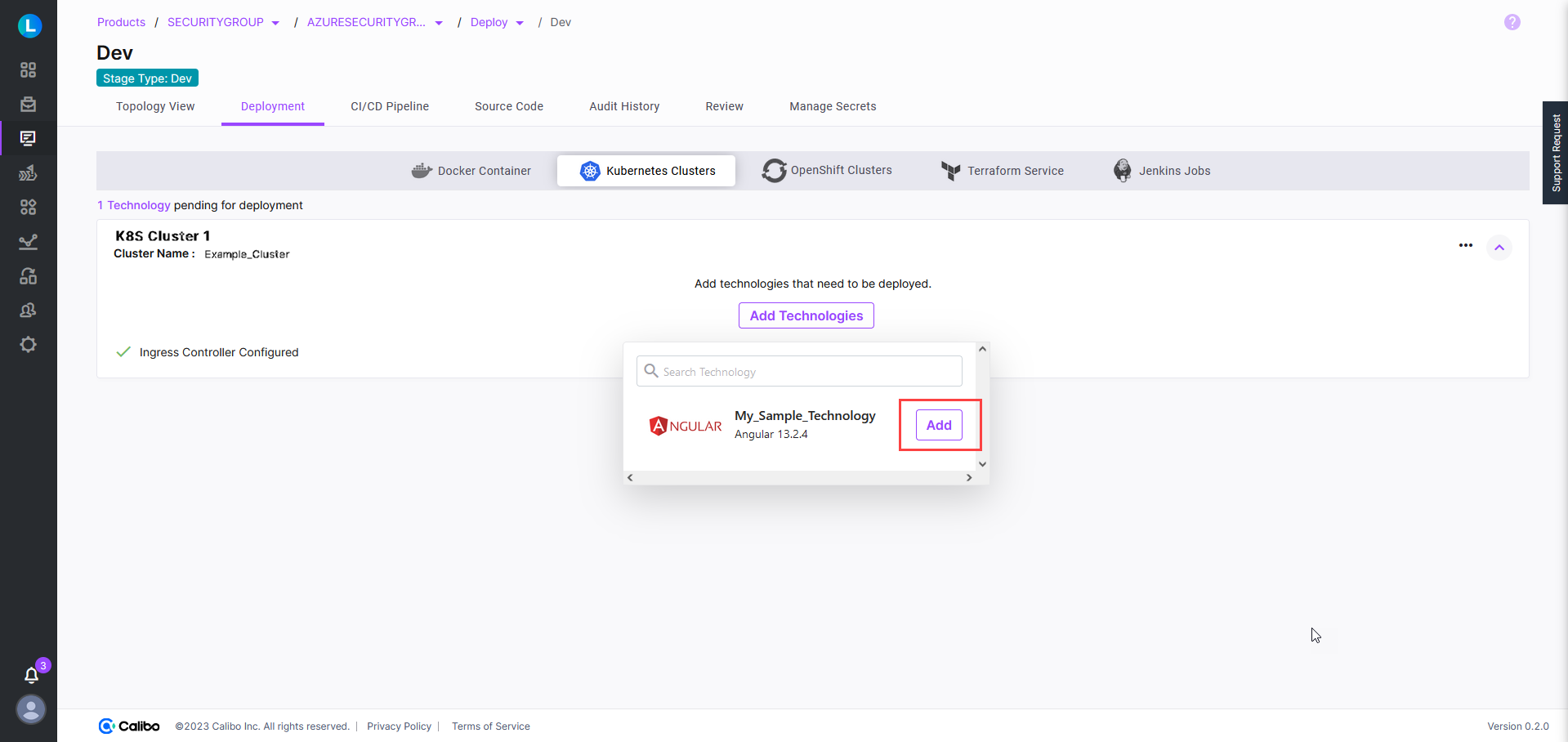
On the Deployment tab, go to the Kubernetes Clusters deployment option.
-
On your configured running Kubernetes cluster, configure an ingress controller by following the on-screen instructions. Ingress controller simplifies the management of external traffic, enhances security, and enables you to configure routing rules for your services within a Kubernetes cluster. It is a fundamental component of exposing and managing Kubernetes workloads to the internet or other external networks. For details, see Configure Ingress Controller.
-
Click Add Technologies, and add the desired technology.
-
Configure all the deployment specifications such as the context path, desired source code branch, Kubernetes cluster namespace where you want to deploy the technology, triggers for CI and CD pipelines, port number, and the minimum and maximum resource allocations for your containers, among others. For details, see Add Technologies to Be Deployed on Kubernetes Cluster.
-
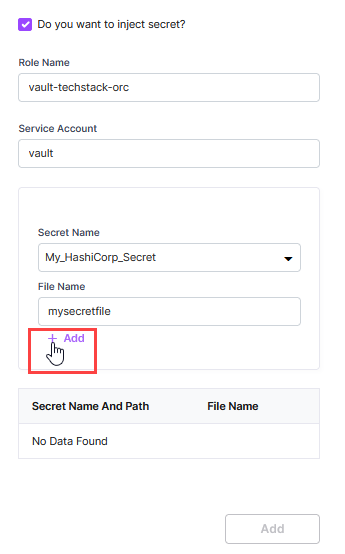
To inject a secret into your application at runtime, turn on the Inject Secret toggle. This option is visible only when you have at least one secret configured on the Manage Secrets tab of your deployment workflow.
Provide the following details:
-
Role Name: Enter your HashiCorp Vault role, which is associated with the Kubernetes service account you use for technology deployment.
-
Service Account: Enter the name of your Kubernetes service account that you use to deploy technologies.
-
Secret Name: Select the desired secret from the list of secrets that you have configured on the Manage Secrets tab.
-
File Name: Provide the name of the file which is loaded into your Kubernetes pod. Secrets are injected into this file at runtime during the deployment of a technology.
Click +Add.
-
-
Click Add to save the technology details you provided.
With this, your technology is ready to be deployed. You can edit the technology details if required. Click Deploy in the upper right corner. As soon as the deployment starts, you can view the progress of the deployment on the CI/CD Pipeline tab.
-
Install and configure HashiCorp Vault Plugin in your Jenkins instance.
-
The authentication token must have the necessary permissions to retrieve (read) information from specific paths or locations within HashiCorp Vault.
-
Go to the stage in the deployment workflow of a product feature where you want to add and deploy technologies.
-
On the Manage Secrets tab, click Add to configure the details of your HashiCorp Vault secret.

-
In the Add Secret side drawer, enter the following details:
-
Secret Name: Provide the name of the secret stored in Vault.
-
Secret Management Tool: Select HashiCorp Vault.
-
Deployment Mode: Choose Docker.
-
URL: Provide your HashiCorp Vault URL.
-
Cred ID: Specify the Jenkins credential ID which contains the Vault token.
-
Path: Specify the path to the secret in HashiCorp Vault. For example, you might store a database password at
/dev/apps/mysecrets/db-password. -
Keys: Specify the secret keys that you want to use during technology deployment.
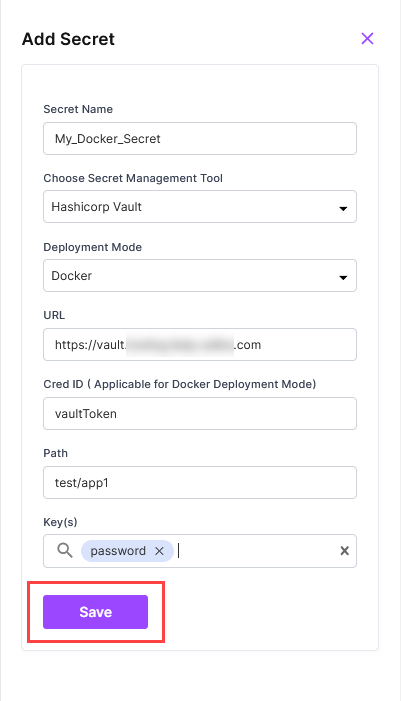
-
On the Manage Secrets tab in a stage in the deployment workflow, you can configure the details of the secrets that you want to dynamically inject into your application at runtime. Currently, we support secret injection from HashiCorp Vault.
To configure your HashiCorp Vault secrets for your Kubernetes deployments from within the Calibo Accelerate platform, do the following:
Enabling Secret Injection During Technology Deployment on Kubernetes
When you add a technology to be deployed in your configured Kubernetes cluster, you can choose to inject a pre-configured secret from HashiCorp Vault. To use the secret injection option, do the following:
Managing Secrets for Technology Deployments on Docker Container
Managing secrets for Docker deployments involves configuring the details of a secret on the Manage Secrets tab of a deployment workflow and enabling HashiCorp secret injection during technology deployment.
Prerequisites
Configuring Secrets in Calibo Accelerate platform
To configure your HashiCorp Vault secrets for your Docker deployments from within the Calibo Accelerate platform, do the following:
Enabling Secret Injection During Technology Deployment on Docker
When you add a technology to be deployed in your configured Docker container, you can choose to inject a pre-configured secret from HashiCorp Vault. To use the secret injection option, do the following:
-
Go to the stage in the deployment workflow of a product feature where you want to add and deploy technologies.
-
On the Deployment tab, go to the Docker Container deployment option.
-
Add and configure a cloud instance. This instance is created in your cloud service provider account preconfigured in Calibo Accelerate by your administrator. See Configure Cloud Instance for Docker Deployment.
-
Click Add Technologies, and add the desired technologies. The technologies that you add and configure in the Develop phase of feature development are listed here.
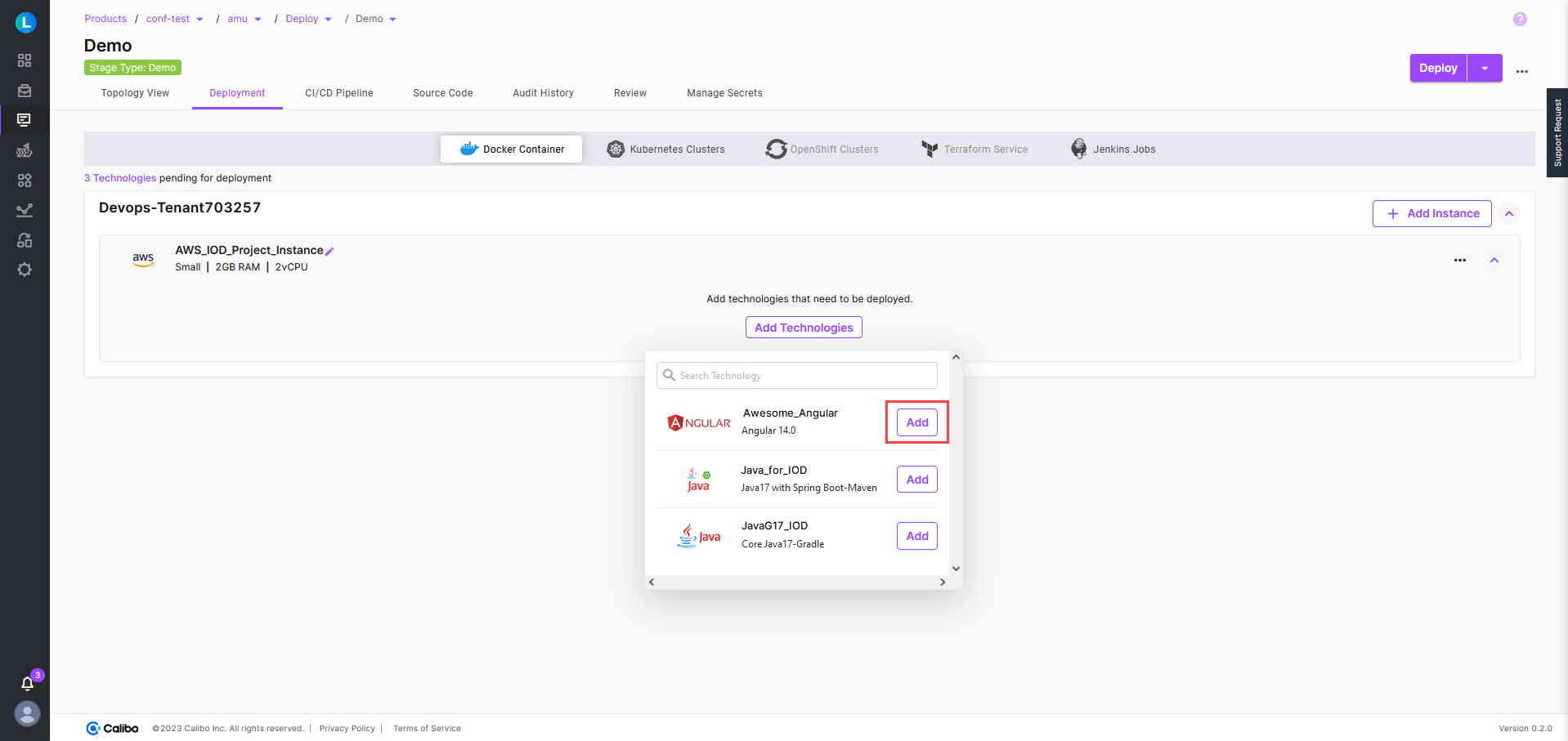
-
Provide all the technology details such as the desired source code branch, context path, and the port number on which your container will listen for incoming network connections. For details, see Add technologies for Docker deployments.
-
To execute functional testing of the technology that is being deployed, turn on the Functional Testing toggle. Select the desired testing tool from the list and provide the details such as desired browser, test case repository URL, test case repository branch, and test case command. This is optional.
-
To inject a secret into your application at runtime, turn on the Inject Secret toggle. This option is visible only when you have at least one secret configured on the Manage Secrets tab of your deployment workflow.
Provide the following details:
-
Secret Name: Select the desired secret from the list of secrets that you have configured on the Manage Secrets tab.
-
Path: The path to the selected secret in HashiCorp Vault is auto-populated.
-
Keys: Select which keys from the stored secret data you want to inject during technology deployment. You may want to map a key with an environment variable where the secret value you want to inject is available.

Note:
The values 'user' and 'passwd' are not allowed as the environment variables.
-
-
Click Add to save the technology details.
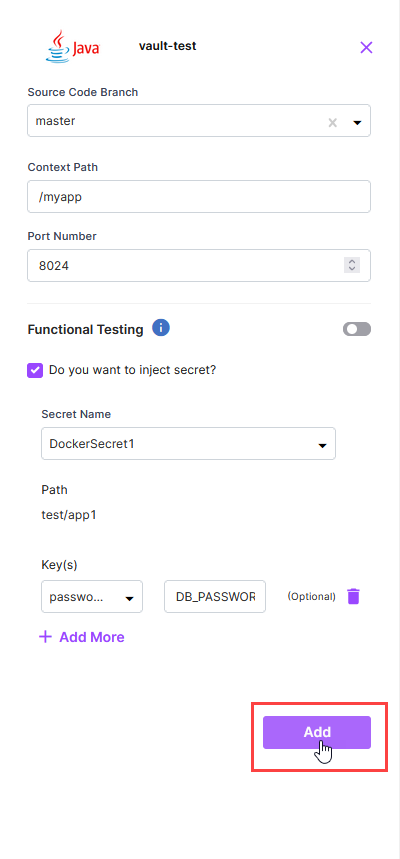
With this, your technology is ready to be deployed. You can edit the technology details if required. Click Deploy in the upper right corner. As soon as the deployment starts, you can view the progress of the deployment on the CI/CD Pipeline tab.
|
What's next? Data Pipeline Studio |