Configure Terraform Connection Details
Terraform is an infrastructure as code (IaC) tool that allows you to define, provision, and manage cloud infrastructure in a declarative configuration language. It is widely used for automating the creation and management of resources like virtual machines, networks, and databases across various cloud providers. By using Terraform, you can ensure consistent, repeatable, and scalable infrastructure provisioning across different environments, streamlining operations and reducing manual errors.
You can execute Terraform scripts from within the Calibo Accelerate platform and provision and manage infrastructure for products you build on the platform. Whether you choose to run your scripts on Terraform Cloud workspaces or directly from a Git repository (such as GitLab, GitHub, or Bitbucket), the first step is to configure Terraform connection details in Calibo Accelerate.
Contents
Required permissions
To successfully connect Calibo Accelerate to Terraform, ensure the user you configure in the connection details has the following specific permissions.
-
For Terraform Cloud
The Team API Token being used in the connection details must have permissions to execute runs and manage workspaces.
-
For Terraform execution using Git repository
To execute Terraform scripts using your Git repositories from the Calibo Accelerate platform interface, the user configured in your source code repository connection details must have the read permissions.
To execute scripts in Terraform Cloud, the Team API Token being used in the connection details must have permissions to execute runs and manage workspaces.
Configuring connection details
To access your Terraform Cloud workspaces or your Git repositories containing your Terraform scripts from within the Calibo Accelerate platform, configure the cluster connection details as described in the following steps:
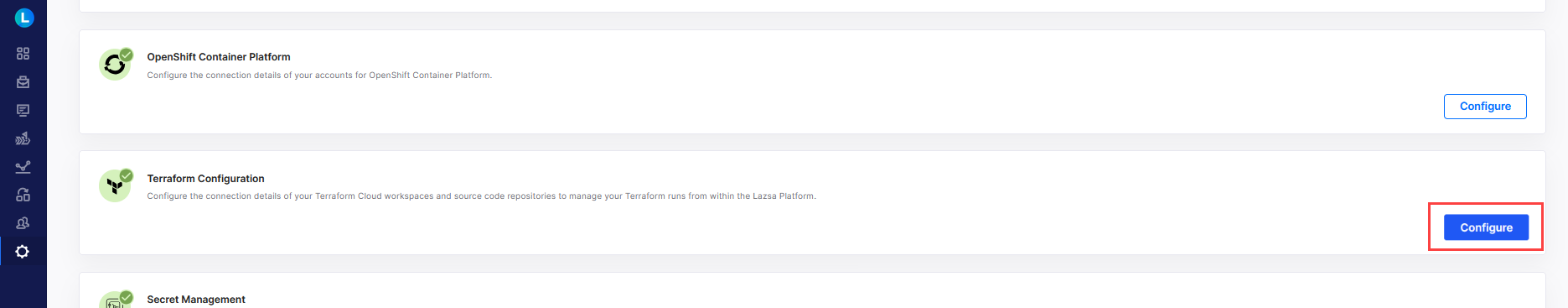
- Sign in to the Calibo Accelerate platform and click Configuration in the left navigation pane.
- On the Platform Setup screen, on the Cloud Platforms, Tools & Technologies tile, click Configure.
- On the Cloud Platforms, Tools & Technologies screen, in the Terraform Configuration section, click Configure.
(After you save your first Terraform connection configuration, you see the Modify button here.)
-
Depending on whether you plan to execute your Terraform workspace runs using Terraform Cloud or want to run Terraform scripts directly from your Git repository using Jenkins, configure the connection details accordingly. On the Terraform Configuration screen, click one of the following tiles:

The choice between using Terraform Cloud or a Git repository to run Terraform scripts from within Calibo Accelerate depends on your project requirements and preferences. Depending on your choice, configure the details as follows:
-
Configure your Terraform Cloud connection details if you want to utilize your pre-configured Terraform Cloud workspace, which is already linked to your VCS provider, working directory, and execution settings and you want to trigger the runs from the deployment workflow in the Calibo Accelerate interface. In this method, your Terraform runs, state files, variables are managed by Terraform Cloud.
 Terraform Cloud
Terraform Cloud
Configure your Terraform Cloud instance connection details as follows.
-
Configuration Name: Give a unique and descriptive name to your Terraform connection configuration. This name will be used to identify and manage the connection details within the Calibo Accelerate platform. Choose a name that clearly represents the environment or project it is associated with so that you can easily identify it in future interactions.
-
Terraform URL: Specify the URL of your Terraform Cloud instance. Providing the correct URL is crucial as it defines the entry point through which Calibo Accelerate will communicate with your Terraform Cloud environment to execute scripts, manage resources, and retrieve state information on your behalf.
-
Organization Name: Enter the name of the Terraform Organization associated with the provided Terraform Cloud URL. The organization in Terraform acts as a container for your workspaces, where configurations, state files, and other resources are managed. By specifying the correct organization name, you ensure that Calibo Accelerate can correctly navigate to the appropriate Terraform workspaces or projects within your environment.
-
The Calibo Accelerate platform requires your Team API Token (with due permissions) to execute Terraform runs on your behalf. Depending on how you want your Terraform Team API Token to be utilized to connect to your Terraform Cloud instance from within the platform, do one of the following:
-
Connect using Calibo Accelerate Orchestrator Agent:
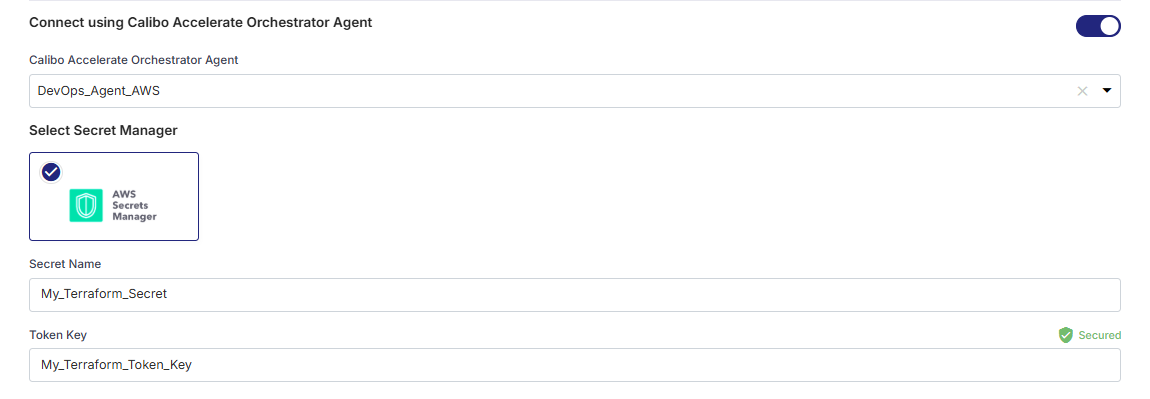
Turn on this toggle to use Calibo Accelerate Orchestrator Agent to programmatically resolve Terraform Cloud team API token stored in your secrets management tool within your private network and to establish communication with your Terraform Cloud instance.
In the Calibo Accelerate Orchestrator Agent dropdown list, all your configured agents are displayed. Select the one you want to use to connect to your Terraform Cloud instance.
The secrets management tool that the selected Orchestrator Agent is authorized to access for retrieving secrets is auto-selected. Specify the details of the Terraform token secret that the agent should retrieve from the secrets management tool. Currently, we support AWS Secrets Manager and Azure Key Vault.
For AWS Secrets Manager, provide the secret name and token key where you store your Terraform team API token.
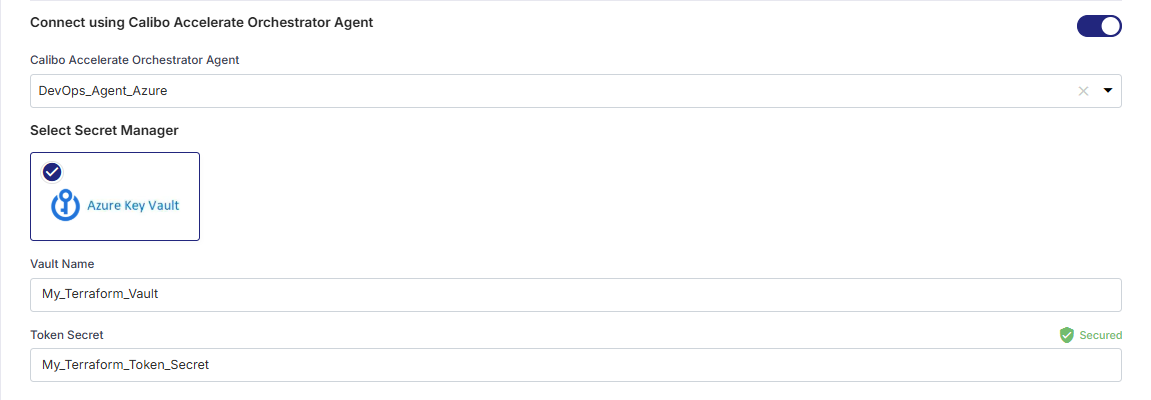
For Azure Key Vault, provide the vault name and the name of secret where store your Terraform team API token.
-
Select Secret Manager
If you don't use the Calibo Accelerate Orchestrator Agent, you can directly provide the team API token in the configuration, or retrieve it from a secrets management tool of your choice (such as AWS Secrets Manager or Azure Key Vault). Do one of the following:
-
Select Calibo Accelerate and enter your Terraform team API token. In this case, your Terraform team API token is securely stored in the Calibo-managed secrets store.
-
Select AWS Secrets Manager. In the Secrets Management Tool dropdown list, the AWS Secrets Manager configurations that you save and activate in the Secret Management section on the Cloud Platforms, Tools & Technologies screen are listed for selection. Select the configuration of your choice. Provide the secret name and the token key for the Calibo Accelerate platform to retrieve the token to connect to your Terraform Cloud instance.
-
Select Azure Key Vault. In the Vault Configuration dropdown list, the Azure Key Vault configurations that you save and activate in the Secret Management section on the Cloud Platforms, Tools & Technologies screen are listed for selection. Select the configuration of your choice. Provide the vault name and token secret for the Calibo Accelerate platform to retrieve the token.
-
-
-
Configure Variable Sets

Note:
First, click Test Connection to check if you can connect to the configured Terraform Cloud instance successfully. Variable sets are fetched from your Terraform Cloud organization and are available for selection in this section only after a successful test connection.
Variable sets are groups of reusable variables created at the organization level. Project-specific and workspace-specific variable sets created for the specified organization on your Terraform Cloud instance are available for selection in this list. Select the ones you want to assign to Terraform Cloud workspaces, which will automatically inherit the variables from the set. Global variable sets are automatically applied to all current and future workspaces within an organization.
-
Secure configuration details with a password
To password-protect your Terraform Cloud connection details, enable the Secure configuration details with a password option, enter a password, and then retype it to confirm. This is optional but recommended. When you share the connection details with multiple users, password protection helps you ensure authorized access to the connection details. -
Test Connection
Click Test Connection to check if you can connect to the configured Terraform Cloud instance successfully. -
After you save and activate the configuration, it is listed on the Terraform Configuration screen. Depending on your access, you can do the following:
-
Edit the Terraform connection configuration.
-
Manage access to the configuration.
-
Deactivate the configuration so that it is not available for use in the Deploy phase.
-
View products and policy templates in which the configuration is being used.
-
Delete an unwanted configuration.
-
-
-
To run Terraform scripts stored in your Git repository, select your Terraform-specific repositories in this configuration. When you run Terraform scripts from the deployment workflow in the Calibo Accelerate interface, you choose from the script source repositories that you save in this configuration. In the method, you manage everything, including the execution process, state files, and CI/CD flow. This gives you maximum flexibility.
 Terraform with a source code repository
Terraform with a source code repository
As an alternative to using Terraform Cloud workspaces, you can also run Terraform scripts directly from your Git repository or using Terraform Cloud.
All you need to do is, specify the source code repositories where you store your Terraform scripts and save the configuration. The configuration will be available at the deployment stage level where you can execute the scripts from the selected source code repositories. To save the configuration, on the Configure Terraform Scripts screen, do the following:
-
Name: Give a unique and intuitive name to your configuration. Choose a name that can be easily identified while selecting Terraform configuration at the deployment stage level.
-
Source Code Repository : If you have already configured the connection details of your source code repository tool in the Calibo Accelerate platform, all the repositories from that tool are fetched and provided in this dropdown list. Select the repositories you want to use to run Terraform scripts.
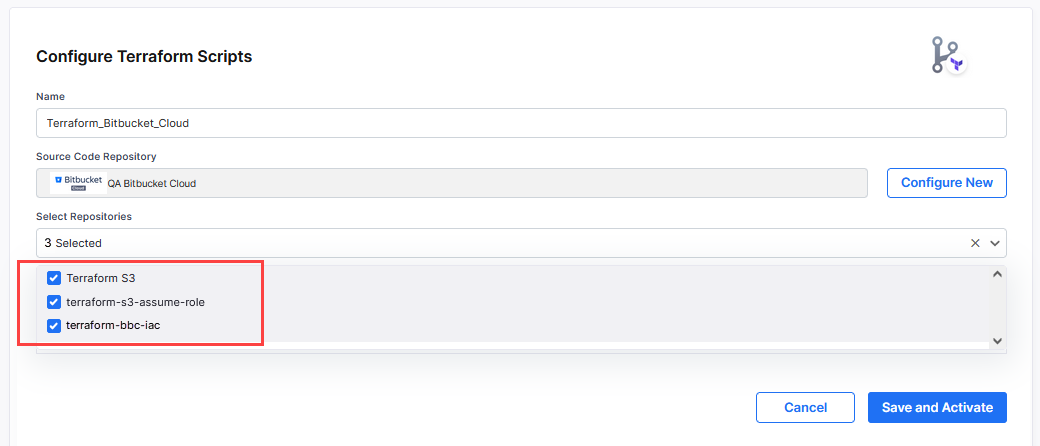
The repositories you selected are listed.
To configure a source code repository tool, click Configure New. For details, see Configure Source Code Repository Connection Details.
-
Provide aliases for repository names (Optional)
For each source code repository you selected in the previous step, you can provide an alias, which means you can assign an easy-to-recognize, user-friendly name to each repository. This makes it simpler to identify and manage repositories within the platform, especially when working with multiple repos. Instead of relying on potentially long or complex repository URLs or names, you can use the alias as a quick reference, reducing the chances of human errors when selecting the correct repository for your Terraform scripts or other tasks.
-
Save and activate the configuration. The configuration is listed on the Terraform Configuration screen. Depending on your access, you can do the following:
-
Edit the configuration.
-
Manage access to the configuration.
-
Deactivate the configuration so that it is not available for use in the Deploy phase.
-
View products and policy templates in which the configuration is being used.
-
Delete an unwanted configuration.
-
-
Thus, you can confiure and save your Terraform-related connection details. For information on how to execute and manage Terraform runs from within the Calibo Accelerate platform, see Managing Terraform Runs from Calibo Accelerate Interface.
-
|
What's next? Configure Connection Details of Secrets Management Tools |