Configure Source Code Repository Connection Details
In today's software development landscape, effective source code management is crucial for collaborative and streamlined development processes. Source code repositories serve as central repositories to store, version, and manage the source code of software projects. Integrating these repositories with your development tools and workflows can significantly enhance productivity, code quality, and team collaboration.
You can access your code base hosted in your source code repositories from within the Calibo Accelerate platform. In the CI/CD View in the Deploy phase, you can also review the commit history and track the progression of your code base. To establish a connection to your source code repository, the Calibo Accelerate platform needs the connection details of the repository.
Currently, the Calibo Accelerate platform supports the following source code repositories:
-
Bitbucket Server
-
GitHub Enterprise Server
-
Bitbucket Cloud
-
GitHub Cloud
To provide the connection details of your active accounts of these source code repositories, follow these steps:
-
Sign in to the Calibo Accelerate platform and click Configuration in the left navigation pane.
-
On the Platform Setup screen, on the Cloud Platform, Tools & Technologies tile, click Configure.
-
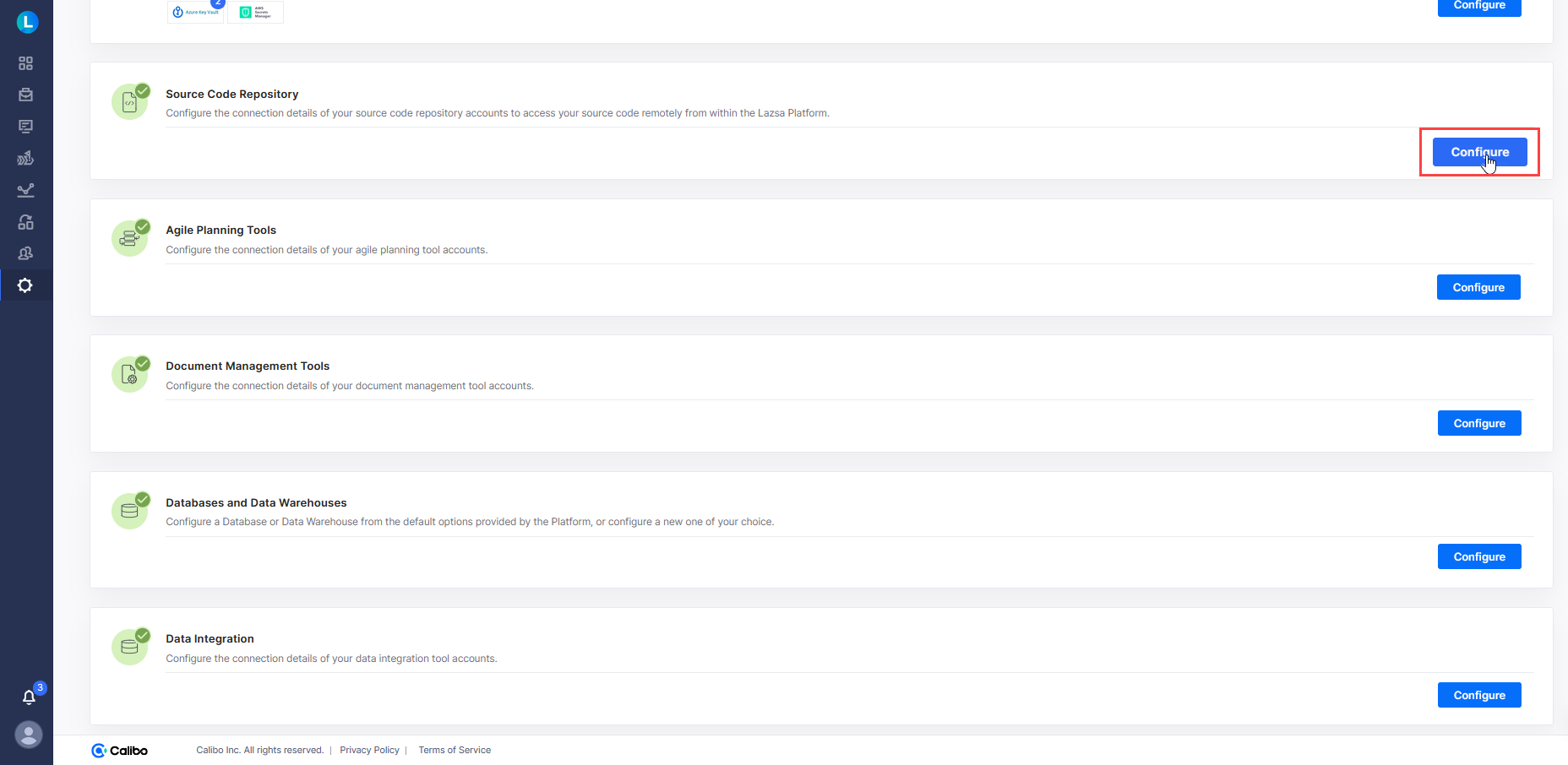
On the Cloud Platform, Tools & Technologies screen, in the Source Code Repository section, click Configure.
(After you save connection details for at least one source code repository account, you see the Modify button here.)
-
On the Source Code Repository screen, click the source code repository of which you want to configure the connection details.
 GitLab
GitLab
Prerequisites and Required Permissions
-
You must have a GitLab account with administrative privileges.
The following table contains the details of the user inputs required in the Calibo Accelerate platform and the permissions that must be assigned to the user account being accessed from the Calibo Accelerate platform.
User Input Required in Calibo Accelerate Required Permissions -
GitLab URL
-
Admin Username
-
Private Token
-
Group Permissions
Read- To read or list groups
-
Repository Permissions
Admin – To create, update, or delete a repository
To save the connection properties of your GitLab account, do the following:
-
Configuration Name: Give a local name to your configuration. Your GitLab connection details are saved by this name in the Calibo Accelerate platform.
-
GitLab URL: Provide your GitLab server URL.
-
Depending on how you want your GitLab credentials to be managed, do one of the following:
-
Connect using Calibo Accelerate Orchestrator Agent:
Turn on this toggle to use Calibo Accelerate Orchestrator Agent to programmatically resolve your GitLab credentials stored in your secrets management tool within your private network and to establish communication with the GitLab instance.
In the Calibo Accelerate Orchestrator Agent dropdown list, all your configured agents are displayed. Select the one you want to use to connect to your GitLab instance.
The secrets management tool that the selected Orchestrator Agent is authorized to access for retrieving secrets is auto-selected. Currently, we support AWS Secrets Manager and Azure Key Vault. Specify the details of GitLab secrets that the agent should retrieve from the secrets management tool.
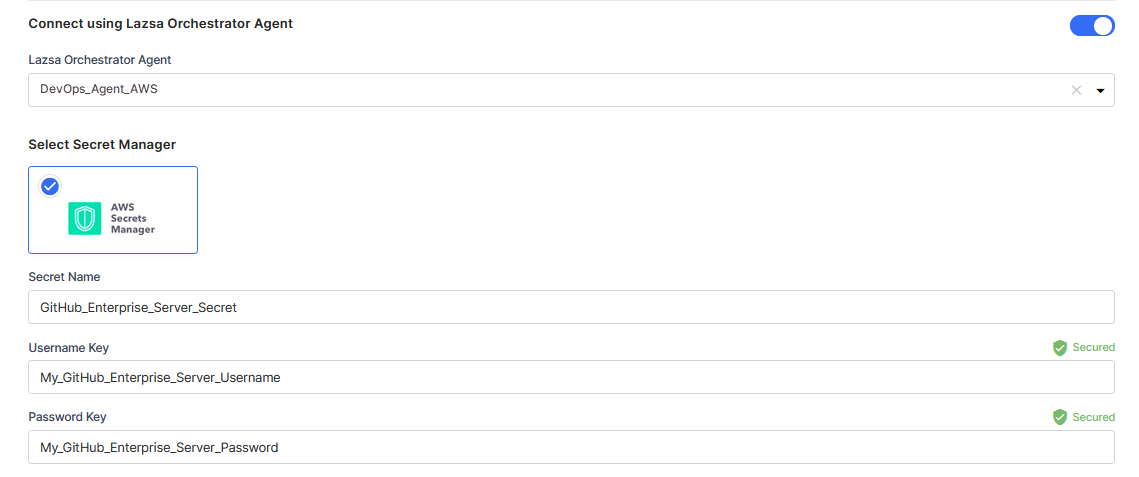
For AWS Secrets Manager, provide the Secret Name, Username Key, and Password Key for your GitLab account credentials.
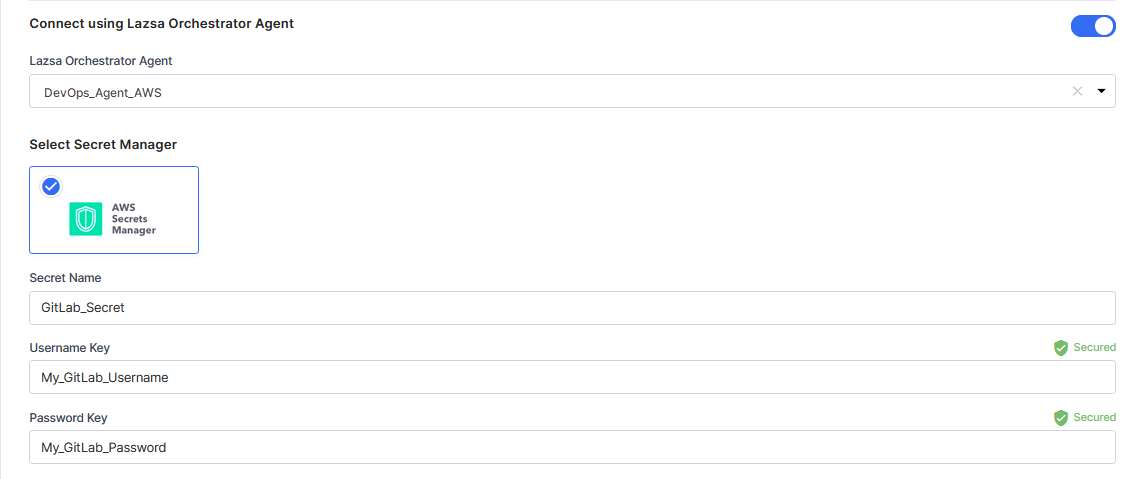
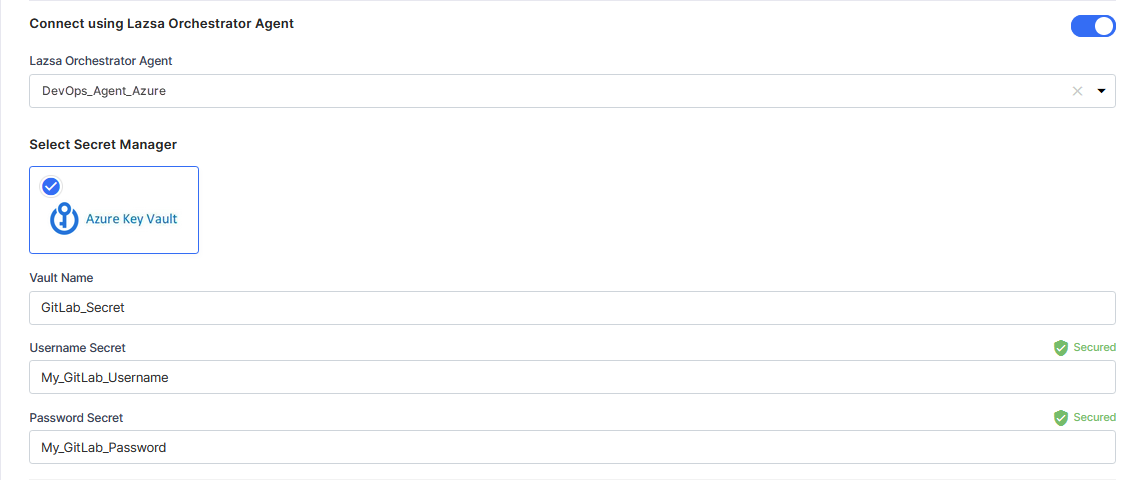
For Azure Key Vault, provide the vault name, username secret, and password secret for your GitLab account credentials.
-
Select Secret Manager
If you don't use the Calibo Accelerate Orchestrator Agent, you can directly provide the credentials in the configuration, or retrieve them from a secrets management tool of your choice (such as AWS Secrets Manager or Azure Key Vault). Do one of the following:
- Select Calibo Accelerate and type your GitLab account Username and Private Token. In this case, credentials are securely stored in the Calibo-managed secrets store.
- Select AWS Secrets Manager. In the Secrets Management Tool dropdown list, the AWS Secrets Manager configurations that you save and activate in the Secret Management section on the Cloud Platform, Tools & Technologies screen are listed for selection. Select your desired secrets management tool configuration. Provide the Secret Name, Username Key, and Password Key for the Calibo Accelerate platform to retrieve the values.
- Select Azure Key Vault. In the Vault Configuration dropdown list, the Azure Key Vault configurations that you save and activate in the Secret Management section on the Cloud Platform, Tools & Technologies screen are listed for selection. Select your desired Vault configuration. Provide the Vault Name, Username Secret, and Password Secret for the Calibo Accelerate platform to retrieve the credential values.
-
- Secure configuration details with a password
To password-protect your GitLab connection details, turn on the Secure configuration details with a password toggle, enter a password, and then retype it to confirm.This is optional but recommended. When you share the connection details with multiple users, password protection helps you ensure authorized access to the connection details.
-
Test Connection
Click Test Connection to check whether you can connect to the configured GitLab server successfully. -
After you save and activate the configured connection details, you can see your saved configuration listed in the Source Code Repository section on the Cloud Platform, Tools & Technologies screen.
 Bitbucket Server
Bitbucket Server

Prerequisites and Required Permissions
-
You must have a Bitbucket account with administrative privileges.
The following table contains the details of the user inputs required in the Calibo Accelerate platform and the permissions that must be assigned to the user account being used in the Calibo Accelerate platform.
User Input Required in Calibo Accelerate Required Permissions -
Base URL
-
Admin Username
-
App Password
-
HTTP Access Token
-
Project Permissions
Admin - To create/ update project
-
Repository Permissions
Admin – To create, update, or delete a repository
To save the connection properties of your Bitbucket Server account, do the following:
-
Configuration Name: Give a local name to your configuration. Your Bitbucket Server connection details are saved by this name in the Calibo Accelerate platform.
-
Base URL: This is the root URL or address used to access the Bitbucket Server instance.
-
Depending on how you want your Bitbucket Server to be managed, do one of the following:
-
Connect using Calibo Accelerate Orchestrator Agent:
Turn on this toggle to use Calibo Accelerate Orchestrator Agent to programmatically resolve the Bitbucket Server credentials stored in your secrets management tool within your private network and to establish communication with the Bitbucket Server instance.
In the Calibo Accelerate Orchestrator Agent dropdown list, all your configured agents are displayed. Select the one you want to use to connect to your Bitbucket Server instance.
The secrets management tool that the selected Orchestrator Agent is authorized to access for retrieving secrets is auto-selected. Currently, we support AWS Secrets Manager and Azure Key Vault. Specify the details of Bitbucket Server secrets that the agent should retrieve from the secrets management tool.
For AWS Secrets Manager, provide the Secret Name, Username Key, Password Key, and Token Key for your Bitbucket Server credentials.
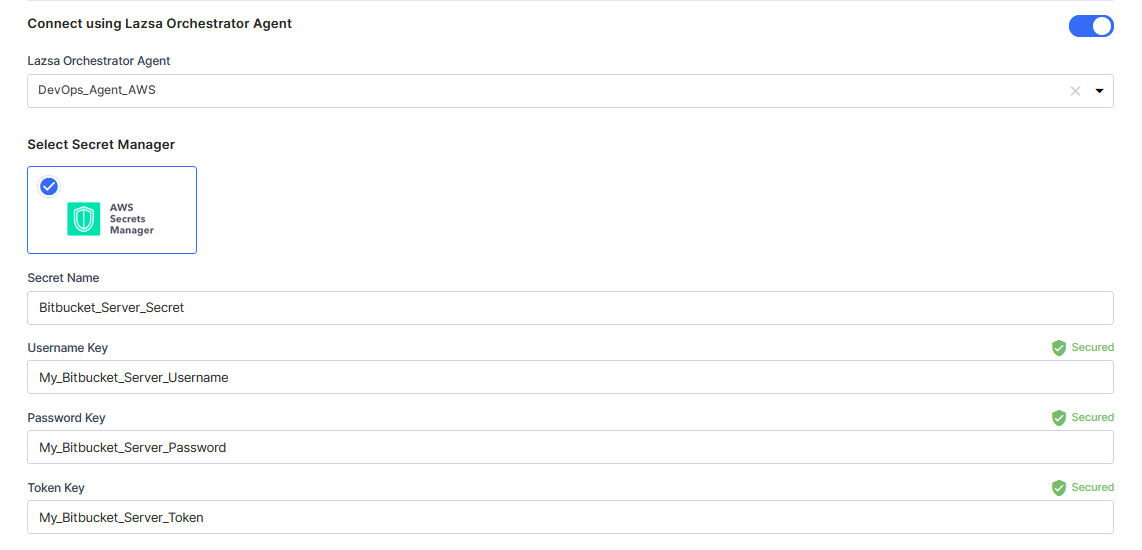
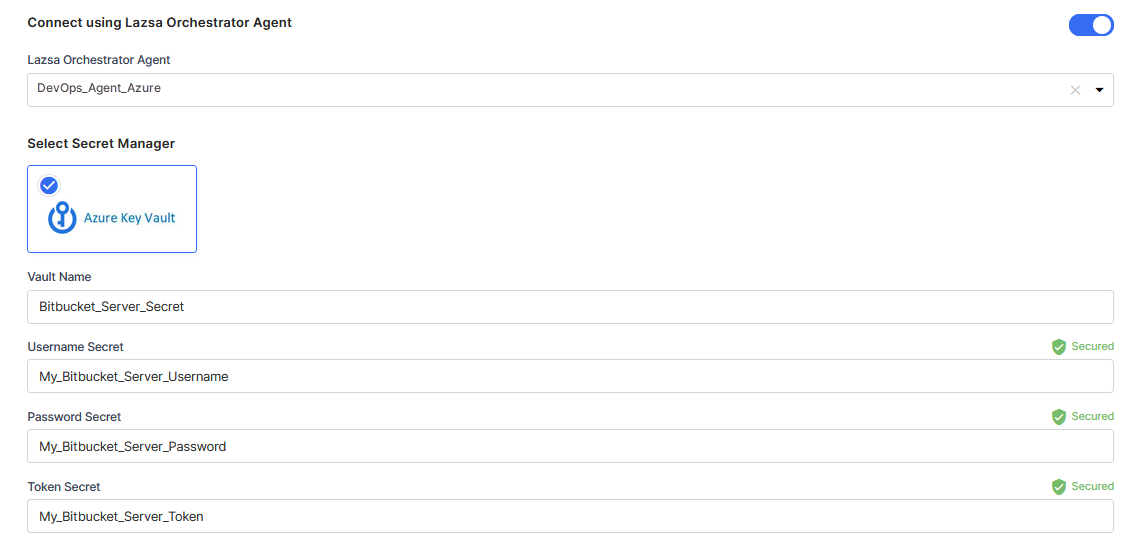
For Azure Key Vault, provide the Vault Name, Username Secret, Password Secret, and Token Secret for your Bitbucket Server credentials.
-
Select Secret Manager
If you don't use the Calibo Accelerate Orchestrator Agent, you can directly provide your Bitbucket Server credentials in the configuration, or retrieve them from a secrets management tool of your choice (such as AWS Secrets Manager or Azure Key Vault). Do one of the following:
- Select Calibo Accelerate and type your Bitbucket Server account Username, Password, and HTTP Access Token. In this case, credentials are securely stored in the Calibo-managed secrets store.
- Select AWS Secrets Manager. In the Secrets Management Tool dropdown list, the AWS Secrets Manager configurations that you save and activate in the Secret Management section on the Cloud Platform, Tools & Technologies screen are listed for selection. Select your desired secrets management tool configuration. Provide the Secret Name, Username Key, Password Key, and Token Key for the Calibo Accelerate platform to retrieve the values.
- Select Azure Key Vault. In the Vault Configuration dropdown list, the Azure Key Vault configurations that you save and activate in the Secret Management section on the Cloud Platform, Tools & Technologies screen are listed for selection. Select your desired secrets management tool configuration. Provide the Vault Name, Username Secret, Password Secret, and Token Secret for the Calibo Accelerate platform to retrieve the credential values.

Note:
If your HTTP access token expires, renew the token in Bitbucket Server and update the renewed token in your Bitbucket Server configuration in the Calibo Accelerate platform.
-
- Secure configuration details with a password
To password-protect your Bitbucket Server connection details, turn on the Secure configuration details with a password toggle, enter a password, and then retype it to confirm.This is optional but recommended. When you share the connection details with multiple users, password protection helps you ensure authorized access to the connection details.
-
Test Connection
Click Test Connection to check whether you can connect to the configured Bitbucket Server instance successfully. -
After you save and activate the configured connection details, you can see your saved configuration listed in the Source Code Repository section on the Cloud Platform, Tools & Technologies screen.
 GitHub Enterprise Server
GitHub Enterprise Server
Prerequisites and Required Permissions
-
You must have a GitHub Enterprise Server account with administrative privileges.
The following table contains the details of the user inputs required in the Calibo Accelerate platform and the permissions that must be assigned to the user account being used in the Calibo Accelerate platform.
User Input Required in Calibo Accelerate Required Permissions -
GitHub URL
-
Admin Username
-
Personal Access Token
-
Organization Permissions
Read- To read repositories within an organization
-
Repository Permissions
Admin – To create, update, or delete a repository
To save the connection properties of your GitHub Enterprise Server account, do the following:
-
Configuration Name: Give a local name to your configuration. Your GitHub Enterprise Server connection details are saved by this name in the Calibo Accelerate platform.
-
GitHub URL: This is the root URL or address used to access the GitHub Enterprise Server instance.
-
Depending on how you want your GitHub Enterprise Server credentials to be managed, do one of the following:
-
Connect using Calibo Accelerate Orchestrator Agent:
Turn on this toggle to use Calibo Accelerate Orchestrator Agent to programmatically resolve the GitHub Enterprise Server credentials stored in your secrets management tool within your private network and to establish communication with the GitHub Cloud instance.
In the Calibo Accelerate Orchestrator Agent dropdown list, all your configured agents are displayed. Select the one you want to use to connect to your GitHub Enterprise Server instance.
The secrets management tool that the selected Orchestrator Agent is authorized to access for retrieving secrets is auto-selected. Currently, we support AWS Secrets Manager and Azure Key Vault. Specify the details of GitHub Enterprise Server secrets that the agent should retrieve from the secrets management tool.
For AWS Secrets Manager, provide the Secret Name, Username Key, and Password Key for your GitHub Enterprise Server credentials.
For Azure Key Vault, provide the Vault Name, Username Secret, and Password Secret for your GitHub Enterprise Server credentials.
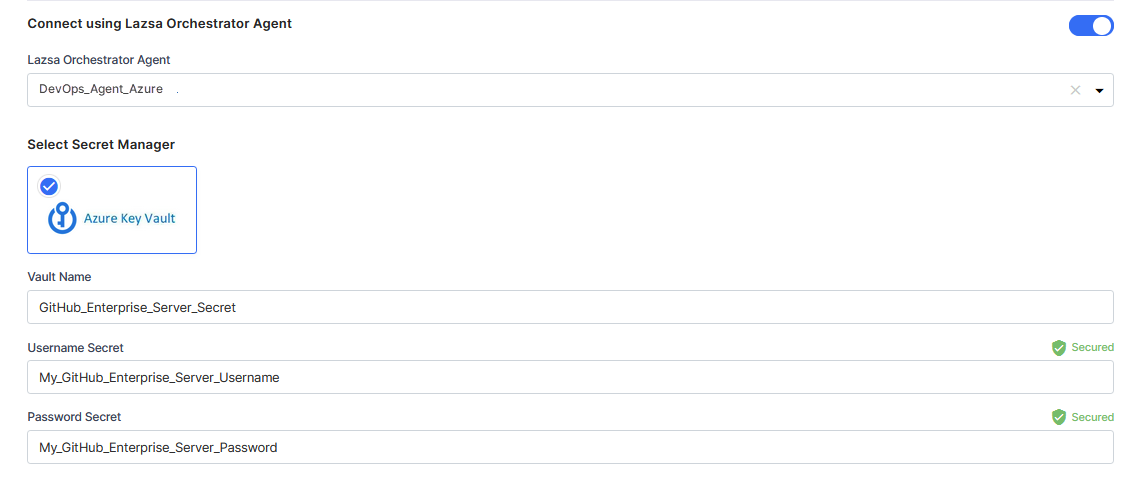
-
Select Secret Manager
If you don't use the Calibo Accelerate Orchestrator Agent, you can directly provide your GitHub Enterprise Server credentials in the configuration, or retrieve them from a secrets management tool of your choice (such as AWS Secrets Manager or Azure Key Vault). Do one of the following:
- Select Calibo Accelerate and type your GitHub Enterprise Server account Username and Personal Access Token. In this case, credentials are securely stored in the Calibo-managed secrets store.
- Select AWS Secrets Manager. In the Secrets Management Tool dropdown list, the AWS Secrets Manager configurations that you save and activate in the Secret Management section on the Cloud Platform, Tools & Technologies screen are listed for selection. Select your desired secrets management tool configuration. Provide the Secret Name, Username Key, and Password Key for the Calibo Accelerate platform to retrieve the secrets.
- Select Azure Key Vault. In the Vault Configuration dropdown list, the Azure Key Vault configurations that you save and activate in the Secret Management section on the Cloud Platform, Tools & Technologies screen are listed for selection. Select your desired secrets management tool configuration. Provide the Vault Name, Username Secret, and Password Secret for the Calibo Accelerate platform to retrieve the credential values.
- Select Calibo Accelerate and type your GitHub Enterprise Server account Username and Personal Access Token. In this case, credentials are securely stored in the Calibo-managed secrets store.
-
- Test Connection
Click Test Connection to check whether you can connect to the configured GitHub Enterprise Server instance successfully. - Organization
After you provide your GitHub Enterprise Server credentials and fill in the other fields, the names of the organizations associated with your GitHub Enterprise Server account are fetched automatically. Choose your desired organization from the list of available organizations.
For technologies that you add in the Develop phase of product development in the Calibo Accelerate platform, repositories are created within the organization that you select here. By associating repositories with the chosen organization, you can ensure that your projects are organized within the appropriate context, facilitating better management and collaboration.
You can also access the existing repositories from the selected organization through the Calibo Accelerate platform interface. - Provide User Mapping
To map Calibo Accelerate user accounts to GitHub Enterprise Server user accounts turn on this toggle. Download the CSV file template available below the drop zone, update user details, and upload the file. - Secure configuration details with a password
To password-protect your GitHub Enterprise Server connection details, enable the Secure configuration details with a password option, enter a password, and then retype it to confirm.This is optional but recommended. When you share the connection details with multiple users, password protection helps you ensure authorized access to the connection details.
-
After you save and activate the configured connection details, you can see your saved configuration listed in the Source Code Repository section on the Cloud Platform, Tools & Technologies screen.
 Bitbucket Cloud
Bitbucket Cloud
Prerequisites and Required Permissions
-
You must have a Bitbucket Cloud account with administrative privileges.
The following table contains the details of the user inputs required in the Calibo Accelerate platform and the permissions that must be assigned to the user account being used in the Calibo Accelerate platform.
User Input Required in Calibo Accelerate Required Permissions -
Base URL
-
Admin Username
-
App Password
-
Workspace Name
-
Project Permissions
Admin - To create/ update project
-
Repository Permissions
Admin – To create, update, or delete a repository
To save the connection properties of your Bitbucket Cloud account, do the following:
-
Configuration Name: Give a local name to your configuration. Your Bitbucket Cloud connection details are saved by this name in the Calibo Accelerate platform.
-
Base URL: This is the root URL or the primary address used to access the Bitbucket Cloud platform. For example, https://bitbucket.org/myorganization/myrepository
-
To provide your Bitbucket Cloud credentials, do one of the following:
-
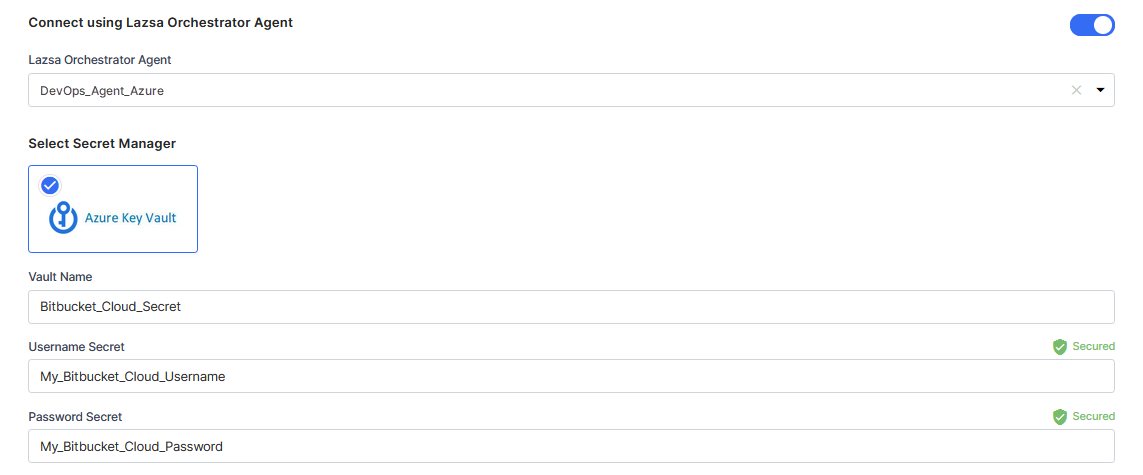
Connect using Calibo Accelerate Orchestrator Agent:
Turn on this toggle to use Calibo Accelerate Orchestrator Agent to programmatically resolve the Bitbucket Cloud credentials stored in your secrets management tool within your private network and to establish communication with the Bitbucket Cloud instance.
In the Calibo Accelerate Orchestrator Agent dropdown list, all your configured agents are displayed. Select the one you want to use to connect to your Bitbucket Cloud instance.
The secrets management tool that the selected Orchestrator Agent is authorized to access for retrieving secrets is auto-selected. Currently, we support AWS Secrets Manager and Azure Key Vault. Specify the details of Bitbucket Cloud secrets that the agent should retrieve from the secret management tool.
For AWS Secrets Manager, provide the Secret Name, Username Key, and Password Key for your Bitbucket Cloud credentials.
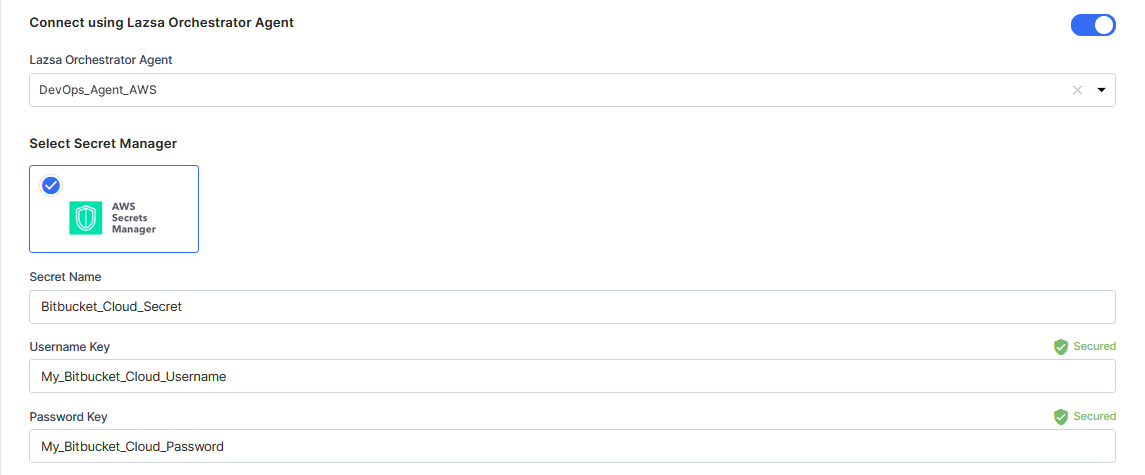
For Azure Key Vault, provide the Vault Name, Username Secret, and Password Secret for your Bitbucket Cloud credentials.
-
Select Secret Manager
If you don't use the Calibo Accelerate Orchestrator Agent, you can directly provide the credentials in the configuration, or retrieve them from a secrets management tool of your choice (such as AWS Secrets Manager or Azure Key Vault). Do one of the following:
- Select Calibo Accelerate and type your Bitbucket Cloud account Username and App Password or Token. In this case, credentials are securely stored in the Calibo-managed secrets store.
- Select AWS Secrets Manager. In the Secrets Management Tool dropdown list, the AWS Secrets Manager configurations that you save and activate in the Secret Management section on the Cloud Platform, Tools & Technologies screen are listed for selection. Select your desired secrets management tools configuration. Provide the Secret Name, Username Key, and Password Key for the Calibo Accelerate platform to retrieve the values.
- Select Azure Key Vault. In the Vault Configuration dropdown list, the Azure Key Vault configurations that you save and activate in the Secret Management section on the Cloud Platform, Tools & Technologies screen are listed for selection. Select your desired secrets management tools configuration. Provide the Vault Name, Username Secret, and Password Secret for the Calibo Accelerate platform to retrieve the credential values.
-
- Workspace
After you fill in all the connection details mentioned earlier, your Bitbucket Cloud workspaces are available for selection. Select the one that you want to connect to from within the Calibo Accelerate platform. When you add technologies in the Develop phase of product development, you can create new repositories in this workspace, or use existing repositories from this workspace. -
Provide User Mapping
To map Calibo Accelerate user accounts to Bitbucket Cloud user accounts, turn on this toggle and then do one of the following:-
Export Bitbucket Cloud users as a CSV file from the Atlassian Admin Portal and upload the file to the drop zone.
-
Download the sample CSV file template available below the drop zone, update user details, and upload the file.
-
- Secure configuration details with a password
To password-protect your Bitbucket Cloud connection details, enable the Secure configuration details with a password option, enter a password, and then retype it to confirm.This is optional but recommended. When you share the connection details with multiple users, password protection helps you ensure authorized access to the connection details.
-
Test Connection
Click Test Connection to check whether you can connect to the configured Bitbucket Cloud instance successfully. -
After you save and activate the configured connection details, you can see them listed in the Source Code Repository section on the Cloud Platform, Tools & Technologies screen.
 GitHub Cloud
GitHub Cloud
Prerequisites and Required Permissions
-
You must have a GitHub Cloud account with administrative privileges.
The following table contains the details of the user inputs required in the Calibo Accelerate platform and the permissions that must be assigned to the GitHub Cloud account being accessed from the Calibo Accelerate platform.
User Input Required in Calibo Accelerate Required Permissions -
GitHub URL
-
Admin Username
-
Personal Access Token
-
Organization Permissions
Read- To read repositories within an organization
-
Repository Permissions
Admin – To create, update, or delete a repository
To save the connection properties of your GitHub Cloud account, do the following:
-
Configuration Name: Give a local name to your configuration. Your GitHub Cloud connection details are saved by this name in the Calibo Accelerate platform.
-
GitHub URL: This is the root URL or address used to access the GitHub Cloud instance.
-
Depending on how you want your GitHub Cloud credentials to be managed, do one of the following:
-
Connect using Calibo Accelerate Orchestrator Agent:
Turn on this toggle to use Calibo Accelerate Orchestrator Agent to programmatically resolve the GitHub Cloud credentials stored in your secrets management tool within your private network and to establish communication with the GitHub Cloud instance.
In the Calibo Accelerate Orchestrator Agent dropdown list, all your configured agents are displayed. Select the one you want to use to connect to your GitHub Cloud instance.
The secrets management tool that the selected Orchestrator Agent is authorized to access for retrieving secrets is auto-selected. Currently, we support AWS Secrets Manager and Azure Key Vault. Specify the details of GitHub Cloud secrets that the agent should retrieve from the secret management tool.
For AWS Secrets Manager, provide the Secret Name, Username Key, and Password Key for your GitHub Cloud credentials.
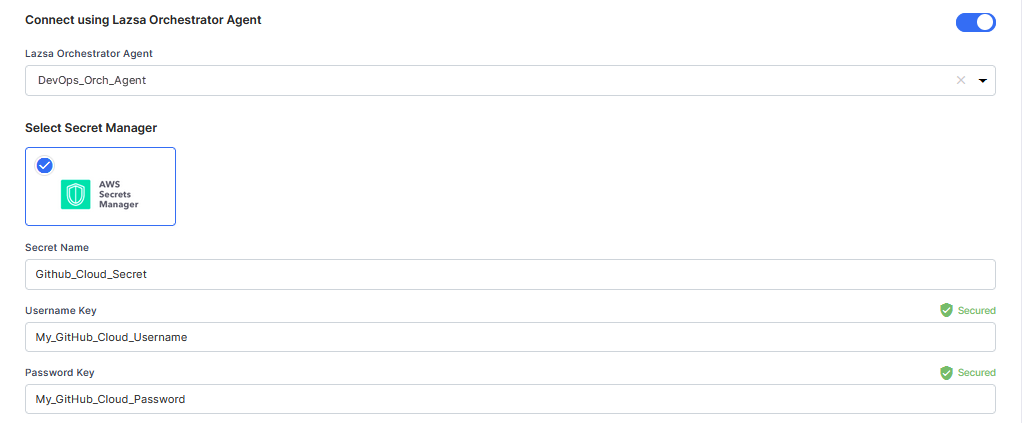
For Azure Key Vault, provide the Vault Name, Username Secret, and Password Secret for your GitHub Cloud credentials.
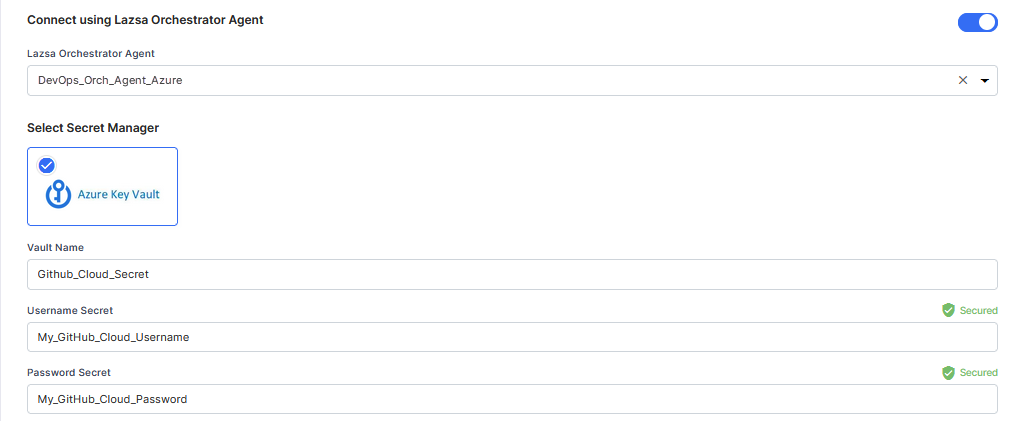
-
Select Secret Manager
If you don't use the Calibo Accelerate Orchestrator Agent, you can directly provide the credentials in the configuration, or retrieve them from a secrets management tool of your choice (such as AWS Secrets Manager or Azure Key Vault). Do one of the following:
- Select Calibo Accelerate and type your GitHub Cloud account Username and Personal Access Token. In this case, credentials are securely stored in the Calibo-managed secrets store.
- Select AWS Secrets Manager. In the Secrets Management Tool dropdown list, the AWS Secrets Manager configurations that you save and activate in the Secret Management section on the Cloud Platform, Tools & Technologies screen are listed for selection. Select your desired secrets management tool configuration. Provide the Secret Name, Username Key, and Password Key for the Calibo Accelerate platform to retrieve the values.
- Select Azure Key Vault. In the Vault Configuration dropdown list, the Azure Key Vault configurations that you save and activate in the Secret Management section on the Cloud Platform, Tools & Technologies screen are listed for selection. Select your desired secrets management tool configuration. Provide the Vault Name, Username Secret, and Password Secret for the Calibo Accelerate platform to retrieve the values.
- Select Calibo Accelerate and type your GitHub Cloud account Username and Personal Access Token. In this case, credentials are securely stored in the Calibo-managed secrets store.
-
- Click Test Connection to check whether you can connect to the configured GitHub Cloud instance successfully.
- Organization :
After you provide your GitHub Cloud credentials and fill in the other fields, the names of the organizations associated with your GitHub Cloud account are fetched automatically. Choose your desired organization from the list of available organizations. By selecting the organization, you choose where repositories for each added technology should be created. Also, existing repositories from the selected organization can also be accessed through Calibo Accelerate. - Provide User Mapping: To map Calibo Accelerate user accounts to GitHub Cloud user accounts, turn on this toggle. Download the sample CSV file template available below the drop zone, update user details, and upload the file.
- To password-protect your GitHub Cloud connection details, enable the Secure configuration details with a password option, enter a password, and then retype it to confirm.
This is optional but recommended. When you share the connection details with multiple users, password protection helps you ensure authorized access to the connection details.
-
After you save and activate the configured connection details, you can see your saved configuration listed in the Source Code Repository section on the Cloud Platform, Tools & Technologies screen.
-
With this, you have completed the configuration of Source Code Repository! You may want to configure the other tools required for product development.
|
What's next? Configure Connection Details of Agile Planning Tools |