Configure Kubernetes Cluster Connection Details
You can deploy your containerized applications on a Kubernetes cluster from within the Calibo Accelerate platform. Here we assume that you already have a running Kubernetes cluster.
Prerequisites and Required Permissions
The following table contains the details of the user inputs required in the Kubernetes cluster connection details in the Calibo Accelerate platform and the permissions that must be assigned to the Kubernetes account.
| User Input Required in Calibo Accelerate | Required Permissions |
|---|---|
|
|
Configuring Cluster Connection Details
To access this cluster from within the Calibo Accelerate platform, you must configure the cluster connection details as described in the following steps:
-
Sign in to the Calibo Accelerate platform and click Configuration in the left navigation pane.
-
On the Platform Setup screen, on the Cloud Platform, Tools & Technologies tile, click Configure.
-
On the Cloud Platform, Tools & Technologies screen, in the Kubernetes section, click Configure.
(After you save your first cluster connection details, you see the Modify button here.)
-
On the Kubernetes Cluster Configuration screen, in the Kubernetes tile, click CONFIGURE.
-
Configure the following cluster connection details and other options:
Configuration Name: Give a name to your configuration. Your Kubernetes cluster connection details are saved by this name in the Calibo Accelerate platform.
Description: Provide a description of your configuration. When you save multiple connection details in the Calibo Accelerate platform, a brief description always helps you identify the saved connection details easily.
Use one of the following options to provide authentication details of your Kubernetes cluster:
Do one of the following:
Fetch cluster connection properties from a configured cloud account
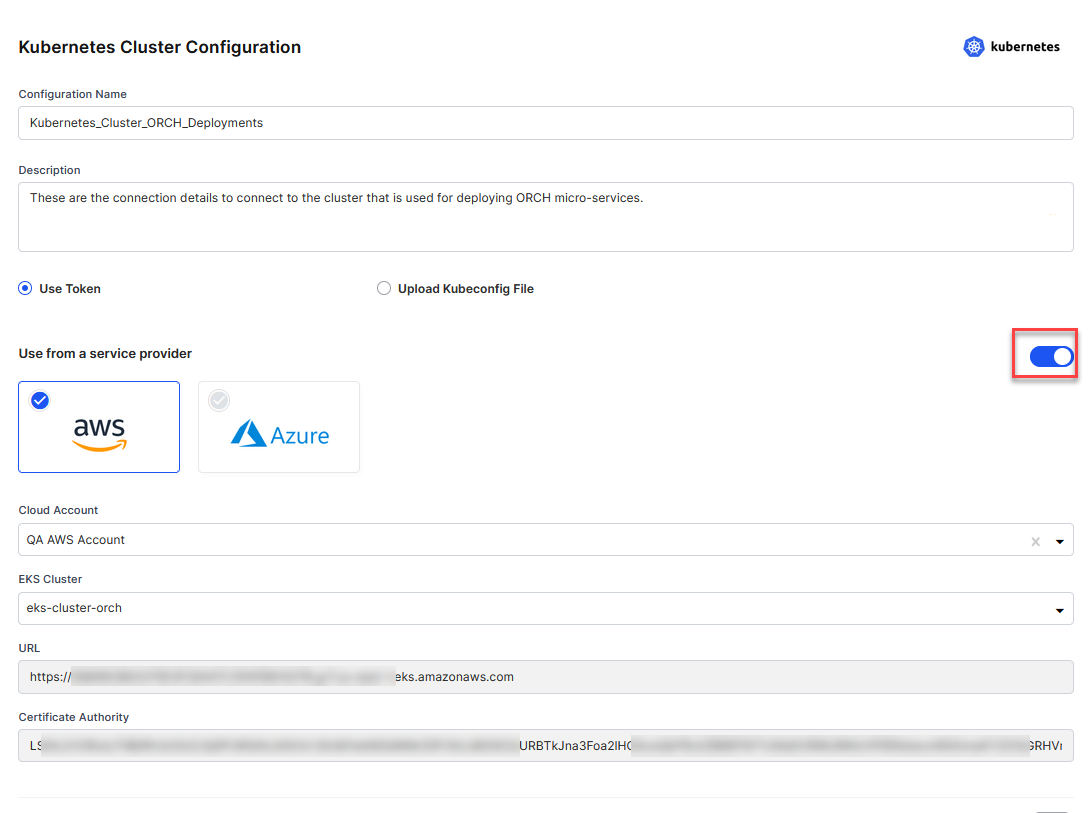
To fetch the details (such as name, URL, and certificate authority data) of a Kubernetes cluster running in your cloud account that you have configured in the Calibo Accelerate platform, enable the Fetch cluster details from cloud account option.
Select the cloud service provider: AWS or Microsoft Azure.
Depending on your selection in the previous step, the AWS or Azure cloud accounts that you have configured in the Calibo Accelerate platform are available for selection in the Cloud Account list. Select the desired cloud account.
Names of Kubernetes clusters that you have configured in the selected cloud account are available for selection in the EKS Cluster list.
After you select the cluster name, the URL to connect to this cluster and its certificate authority data are auto-populated.
Enter connection properties manually
To add connection details of a Kubernetes cluster other than the ones running on the cloud accounts configured in the Calibo Accelerate platform, keep the Fetch cluster details from cloud account option disabled, and manually enter the Cluster Name, API Server URL, and the Certificate Authority data for the cluster.
Depending on how you want your Kubernetes credentials to be managed, do one of the following:
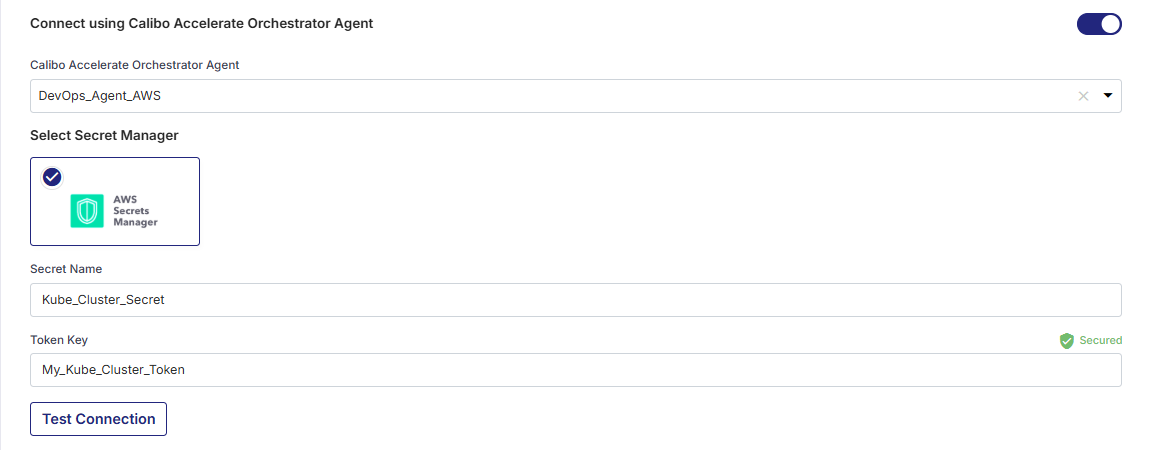
Connect using Calibo Accelerate Orchestrator Agent
Turn on this toggle to use Calibo Accelerate Orchestrator Agent to programmatically resolve the Kubernetes token value stored in your secrets management tool within your private network and to establish communication with your Kubernetes cluster.In the Calibo Accelerate Orchestrator Agent dropdown list, all your configured agents are displayed. Select the one you want to use to connect to your Kubernetes cluster.
The secrets management tool (AWS Secrets Manager or Azure Key Vault) associated with the selected agent is auto-selected. Specify the details of Kubernetes secrets that the agent should retrieve from the secrets management tool.
For AWS Secrets Manager, provide the Secret Name and Token Key where you store your Kubernetes authentication token, and then click Test Connection to check if you can connect to the configured Kubernetes cluster successfully.
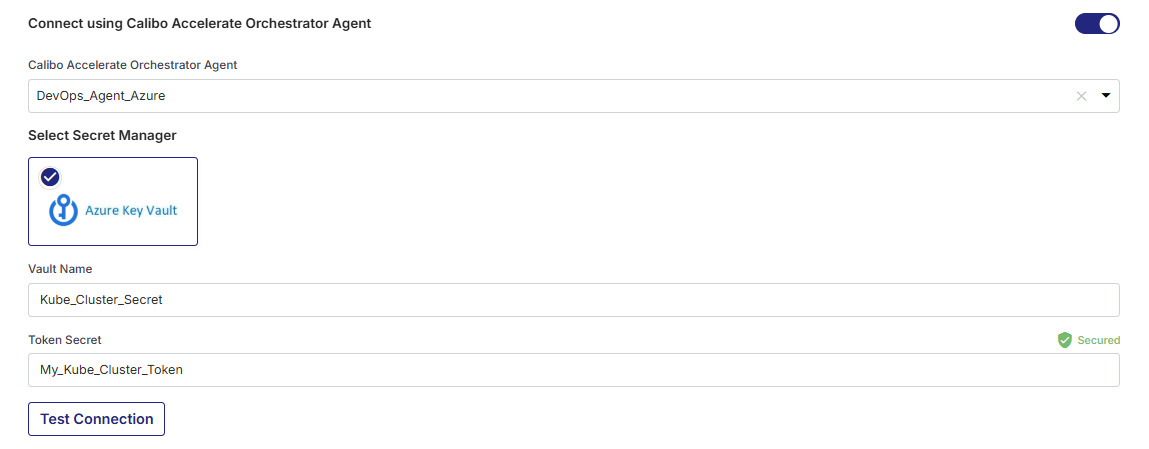
For Azure Key Vault, provide the Vault Name and the name of the secret where you have stored the token, and then click Test Connection to check if you can connect to the configured Kubernetes cluster successfully.
Select Secret Manager (If not using Orchestrator Agent)
If you don't use the Calibo Accelerate Orchestrator Agent, you can directly provide your Kubernetes token in the configuration, or retrieve it from your secrets management tool (such as AWS Secrets Manager or Azure Key Vault).
Do one of the following:
Option 1: Calibo Accelerate (built-in secrets store)
Select Calibo Accelerate and in the Token field, provide the authentication token. In this case, the token is securely stored in the Calibo-managed secrets store.
Then click Test Connection to check whether you can connect to the configured Kubernetes cluster successfully.
Option 2: AWS Secrets Manager
Select AWS Secrets Manager. In the Secrets Management Tool dropdown list, the AWS Secrets Manager configurations that you save and activate in the Secret Management section on the Cloud Platform, Tools & Technologies screen are listed for selection.
Select your desired configuration. Provide the Secret Name and the Token Key where you have stored the token.
Then click Test Connection to check whether you can connect to the configured Kubernetes cluster successfully.
Select Azure Key Vault. In the Vault Configuration dropdown list, the Azure Key Vault configurations that you save and activate in the Secret Management section on the Cloud Platform, Tools & Technologies screen are listed for selection.
Select the configuration of your choice. Provide the vault name and the name of the secret where you have stored the token.
Then click Test Connection to check whether you can connect to the configured Kubernetes cluster successfully.
Provide the name of your running Kubernetes cluster that you want to access from within the Calibo Accelerate platform.
Depending on where you want to store the Kubeconfig file, do one of the following:
Connect using Calibo Accelerate Orchestrator Agent
Turn on this toggle to use Calibo Accelerate Orchestrator Agent to programmatically resolve the details in the Kubeconfig file stored in your secrets management tool within your private network and to establish communication with your Kubernetes cluster.
In the Calibo Accelerate Orchestrator Agent dropdown list, all your configured agents are displayed. Select the one you want to use to connect to your Kubernetes cluster.
The secrets management tool associated with the selected agent is auto-selected. Currently, we support AWS Secrets Manager as the secrets management tool to store your Kubeconfig file. Provide the name of the secret in AWS Secrets Manager where you store the Kubeconfig file details.

Note:
Currently, Azure Key Vault is not supported for the Upload Kubeconfig File option. If you use Azure Key Vault, go ahead with the Use Token option instead.
Click Test Connection to check if you can connect to the configured Kubernetes cluster successfully.
Select Secret Manager (If not using Orchestrator Agent)
If you don't use the Calibo Accelerate Orchestrator Agent, you can directly upload the Kubeconfig file in the configuration, or retrieve it from AWS Secrets Manager.
Do one of the following:
Option 1: Calibo Accelerate (built-in secrets store)
Select Calibo Accelerate and upload the Kubeconfig file in the drop zone. In this case, the Kubeconfig file is securely stored in the Calibo-managed secrets store.
Then click Test Connection to check whether you can connect to the configured Kubernetes cluster successfully.
Select AWS Secrets Manager. In the Secrets Management Tool dropdown list, the AWS Secrets Manager configurations that you save and activate in the Secret Management section on the Cloud Platform, Tools & Technologies screen are listed for selection.
Select the configuration of your choice. In the Secret Name field, provide the name of the secret where you have stored the Kubeconfig file as plain text.

Note:
Currently, Azure Key Vault is not supported for the Upload Kubeconfig File option. If you use Azure Key Vault, go ahead with the Use Token option instead.
Then click Test Connection to check whether you can connect to the configured Kubernetes cluster successfully.
Ingress Controller Configurations (Optional)
In this section, you can add the details of ingress controllers that can be used as predefined configurations for the deployments that are done in your Kubernetes cluster from within the Calibo Accelerate platform.
Note:
The ingress controller configurations you add or modify here take effect only after you save and activate the Kubernetes cluster connection configuration. Ensure the cluster connection is successfully validated using the Test Connection button before proceeding.
As per your requirements and policies, you can allow or restrict modifications to this configuration at a stage level in the Deploy phase.
For detailed information on how to configure ingress controller details, see Configuring Ingress Controllers for Kubernetes Clusters.
- Secure configuration details with a password
To password-protect your Kubernetes cluster connection details, enable the Secure configuration details with a password option, enter a password, and then retype it to confirm.This is optional but recommended. When you share the connection details with multiple users, password protection helps you ensure authorized access to the connection details.
After you save and activate the configured connection details, you can see them listed on the Cloud Platform, Tools & Technologies screen.
 Use Token
Use TokenWith this option, you can use the authentication token to authenticate to your Kubernetes cluster. Perform these steps to enter the cluster details and use the token options.
 Upload Kubeconfig File
Upload Kubeconfig FileKubeconfig file is a YAML file that contains the Kubernetes cluster details, certificate authority data, and the secret token to authenticate the cluster. You can use a Kubeconfig file to establish a connection with your running Kubernetes cluster from within the Calibo Accelerate platform. To connect with your Kubernetes cluster by using the Kubeconfig file, do the following:
With this, you are all set to connect with your Kubernetes cluster from within the Calibo Accelerate platform. You can select this cluster when you deploy your tech stack. You may want to configure the next tool required for your product development.
| What's next? Configure Source Code Repository Connection Details |