Creating a Relying Party Trust in the AD FS Management Console
Creating a Relying Party Trust (RPT) in Active Directory Federation Services (AD FS) establishes a secure trust relationship between the AD FS server and the Calibo Accelerate platform, which relies on AD FS for user authentication. This trust enables Single Sign-On (SSO) functionality, where AD FS authenticates users before granting them access to the Calibo Accelerate platform.
Prerequisites
Ensure you have the Federation Metadata XML file downloaded from the Calibo Accelerate platform. After you complete the SSO configuration steps for Microsoft Active Directory in the First 24 Hours (F24H) Wizard, this file is available for downloading. This file contains the necessary configuration data to establish the trust.
For the configuration steps in the F24H Wizard, see First 24 Hours (F24H) Wizard (For Tenant Administrator).
Creating AD FS Relying Party Trust
To create a relying party trust in the AD FS management console, do the following:
-
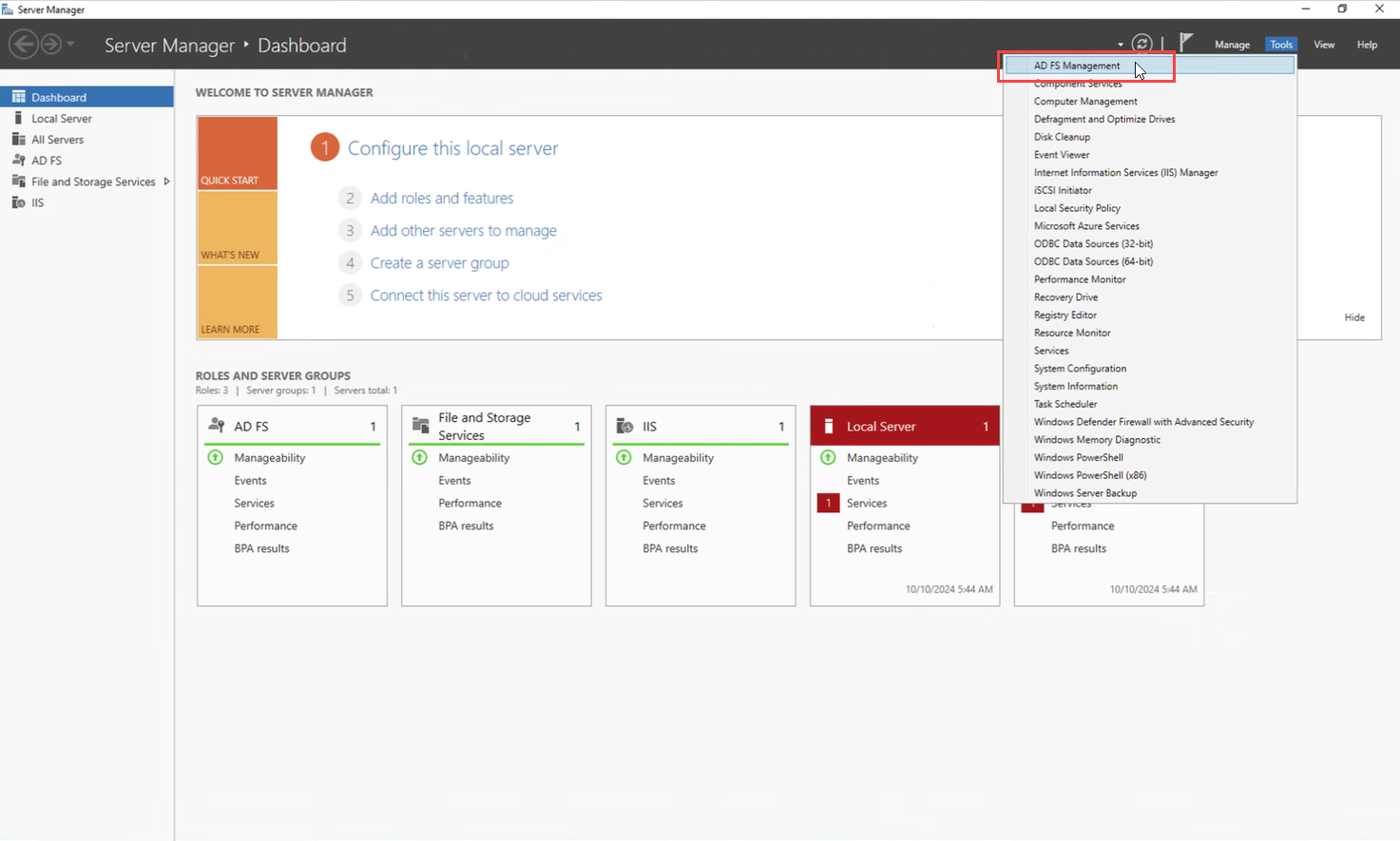
Open AD FS Management Console
Log in to the ADFS server and open the management console. In Server Manager, click Tools and select AD FS Management.
-
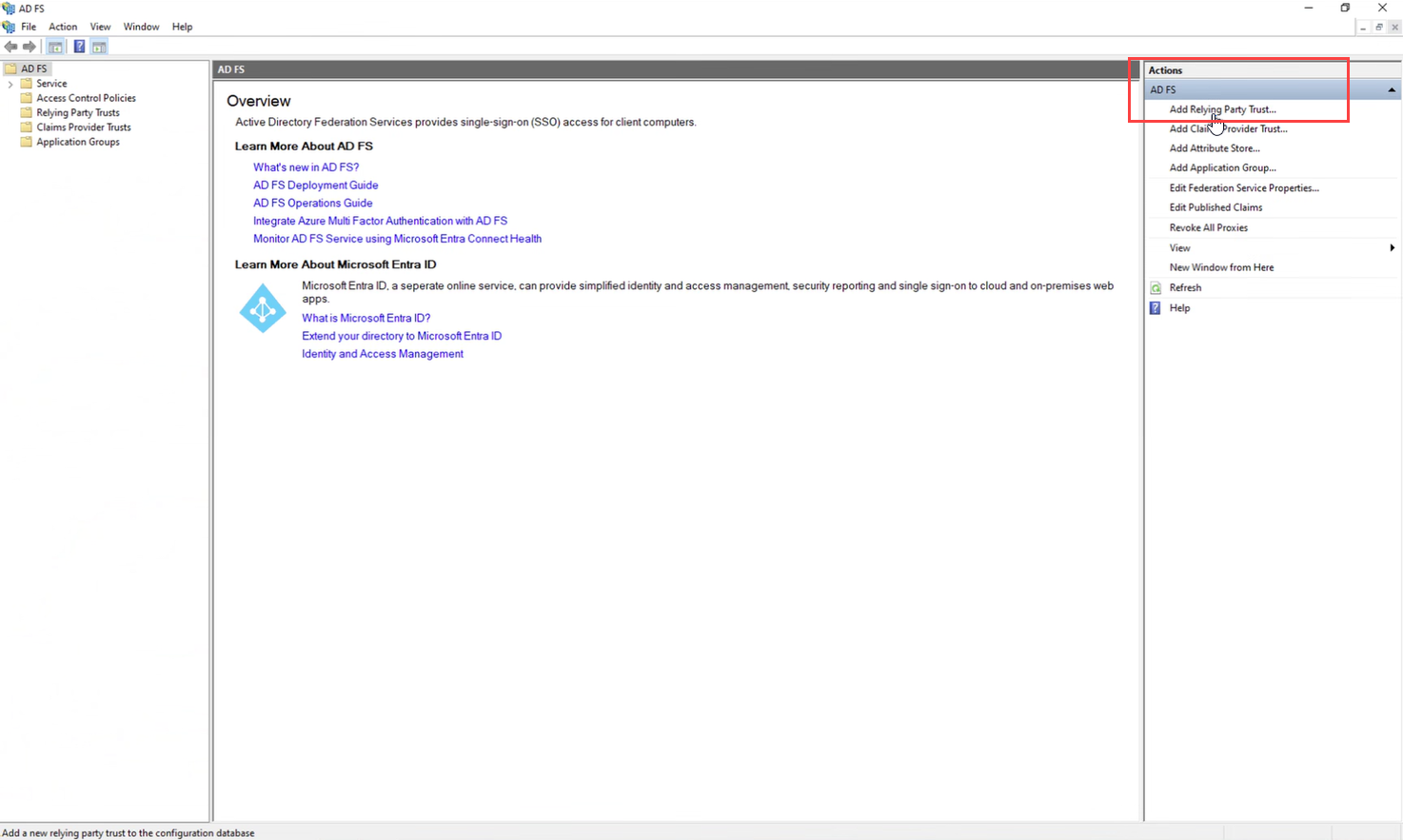
Click Add Relying Party Trust
Under the Actions pane, click Add Relying Party Trust... to start the wizard.
-
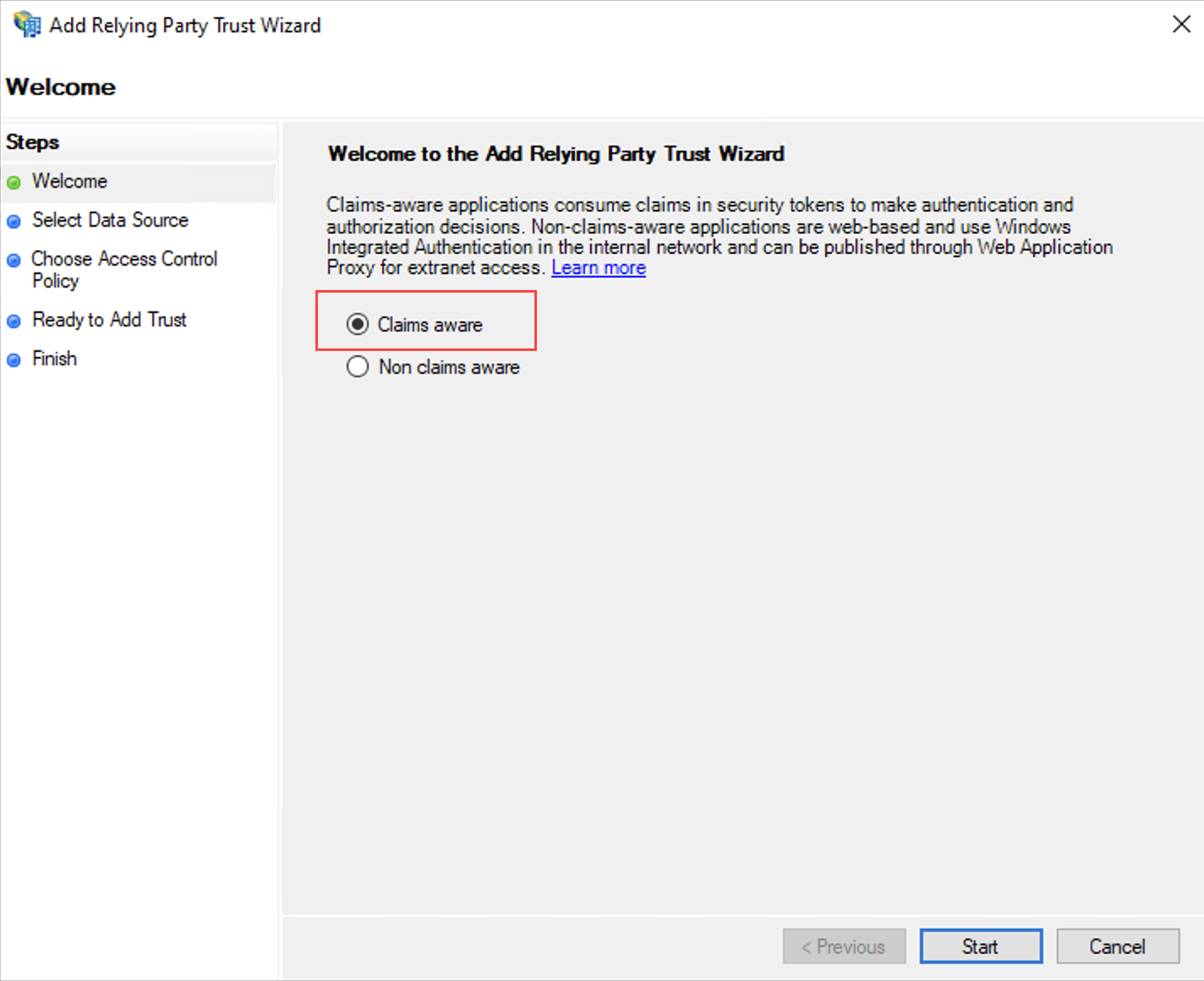
Welcome Page
On the Welcome page, select Claims aware and click Start.
-
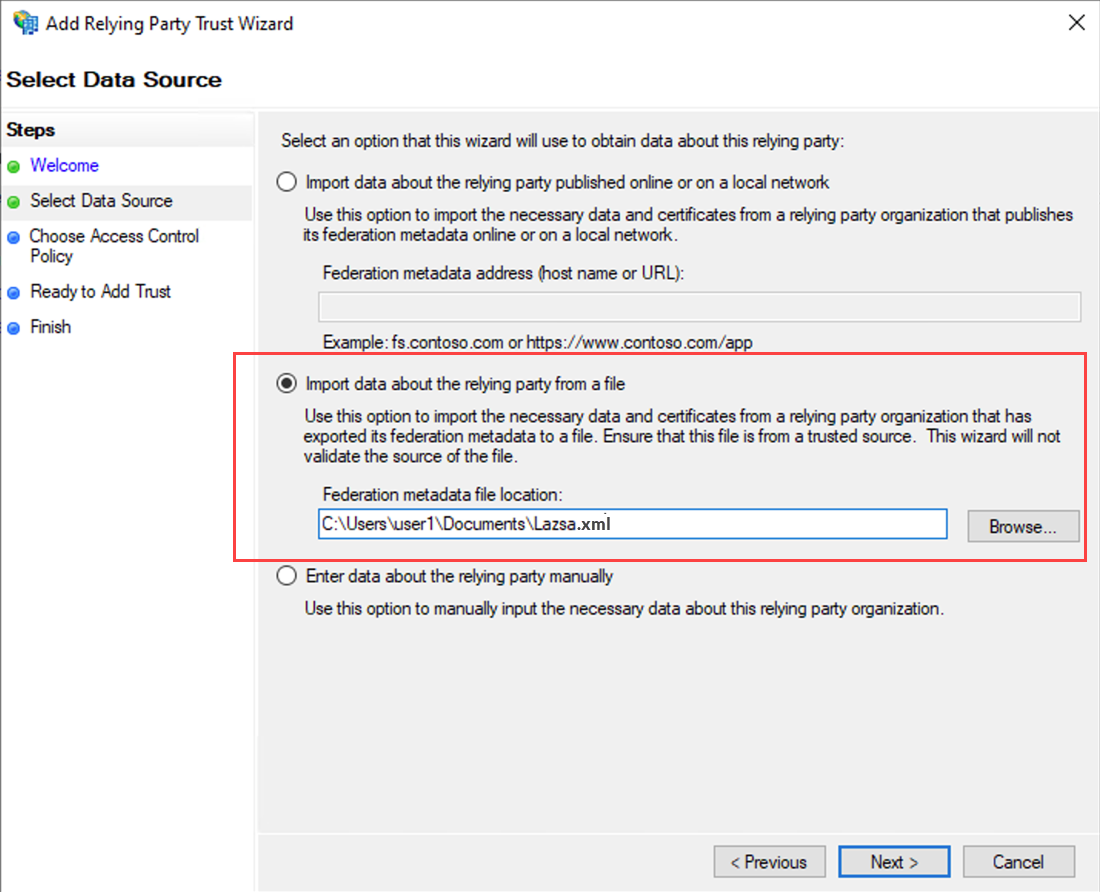
Select Data Source
On the Select Data Source page, choose Import data about the relying party from a file.
Browse to locate the Federation Metadata XML file downloaded from the Calibo Accelerate platform, and click Next.
-
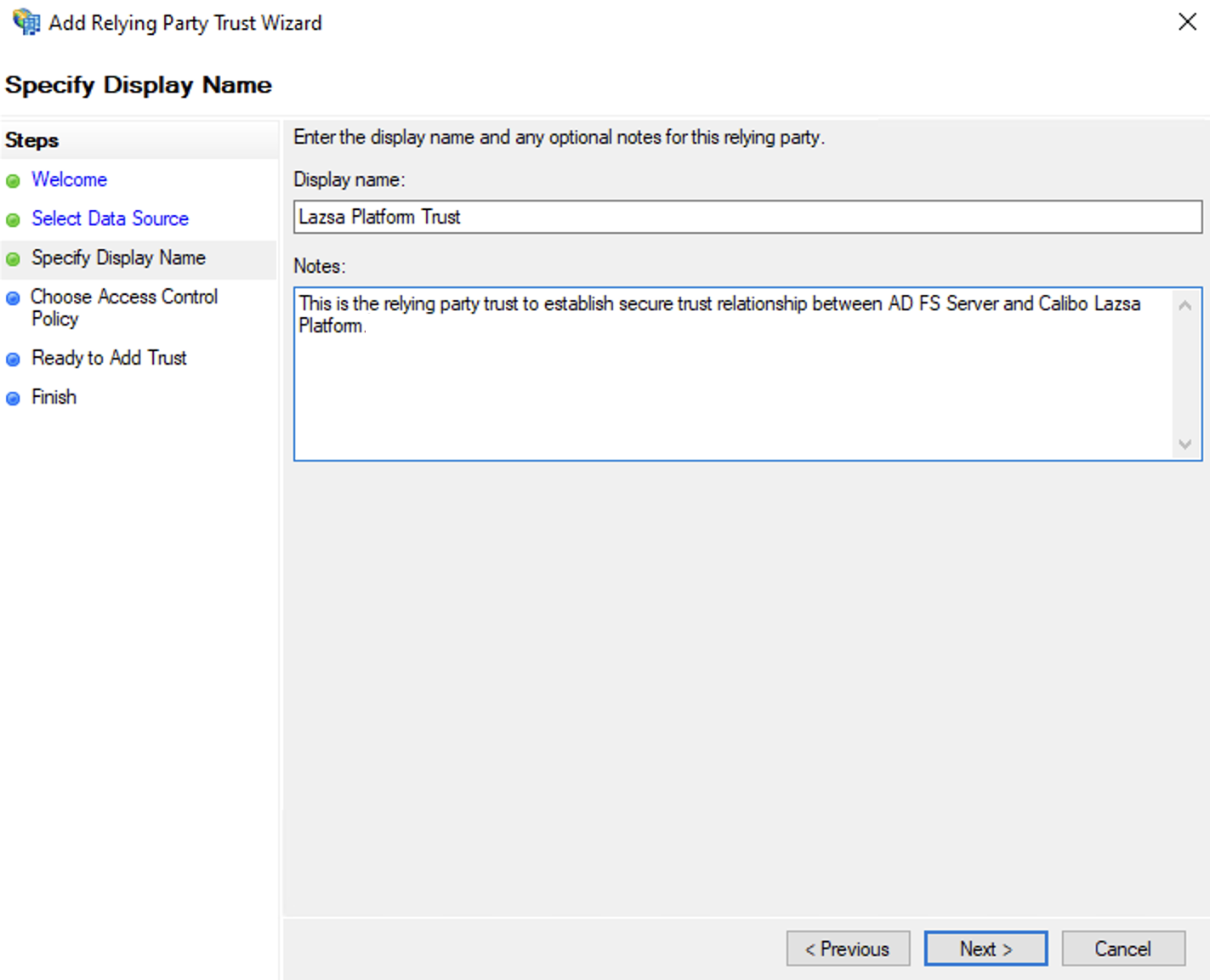
Specify Display Name
On the Specify Display Name page, enter a name in the Display name field (for example, Calibo Accelerate Platform Trust).
Optionally, add a description in the Notes field for future reference.
Click Next to proceed.
-
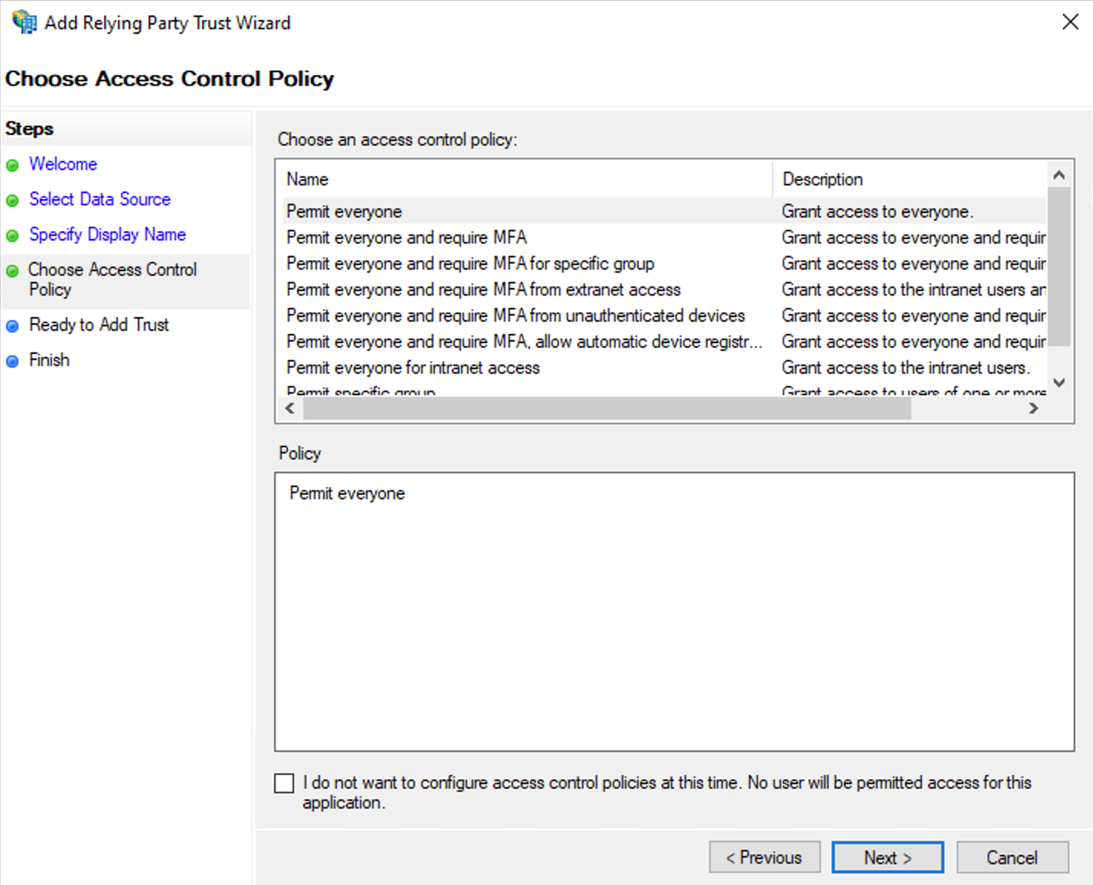
Choose Access Control Policy
On the Choose Access Control Policy page, select the desired access control policy (for example, Permit everyone or a custom policy for user access).
Click Next.
-
Ready to Add Trust
Review the settings on the Ready to Add Trust page, then click Next to complete the creation of the relying party trust.
-
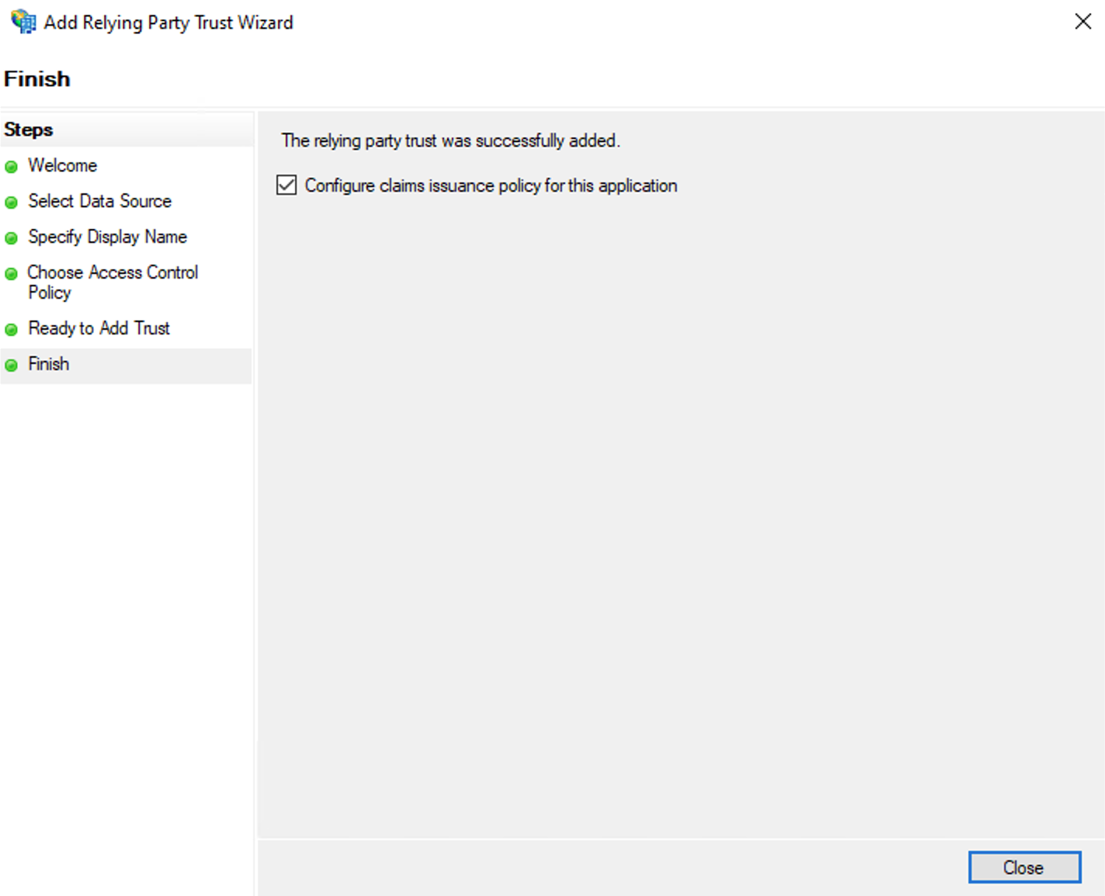
Finish
On the Finish page, click Close. This action will automatically display the Edit Claim Rules dialog box.
-
Edit Claim Issuance Policy
Right-click the trust you just created, and click Edit Claim Issuance Policy.
-
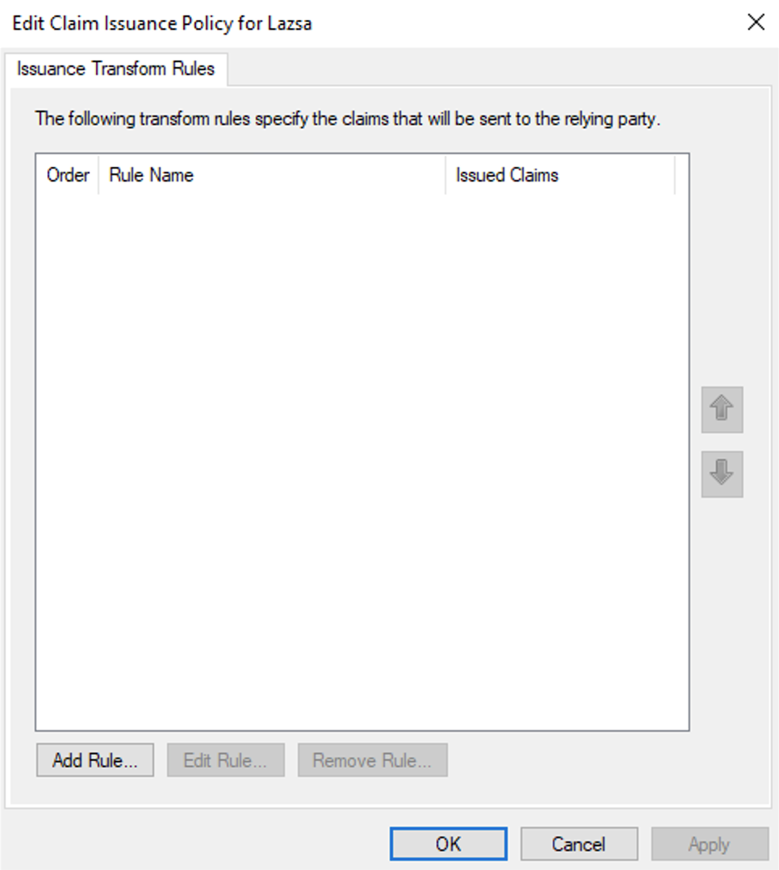
Add Claim Rule
In the Edit Claim Issuance Policy dialog box, under Issuance Transform Rules, click Add Rule to start the rule wizard.
-
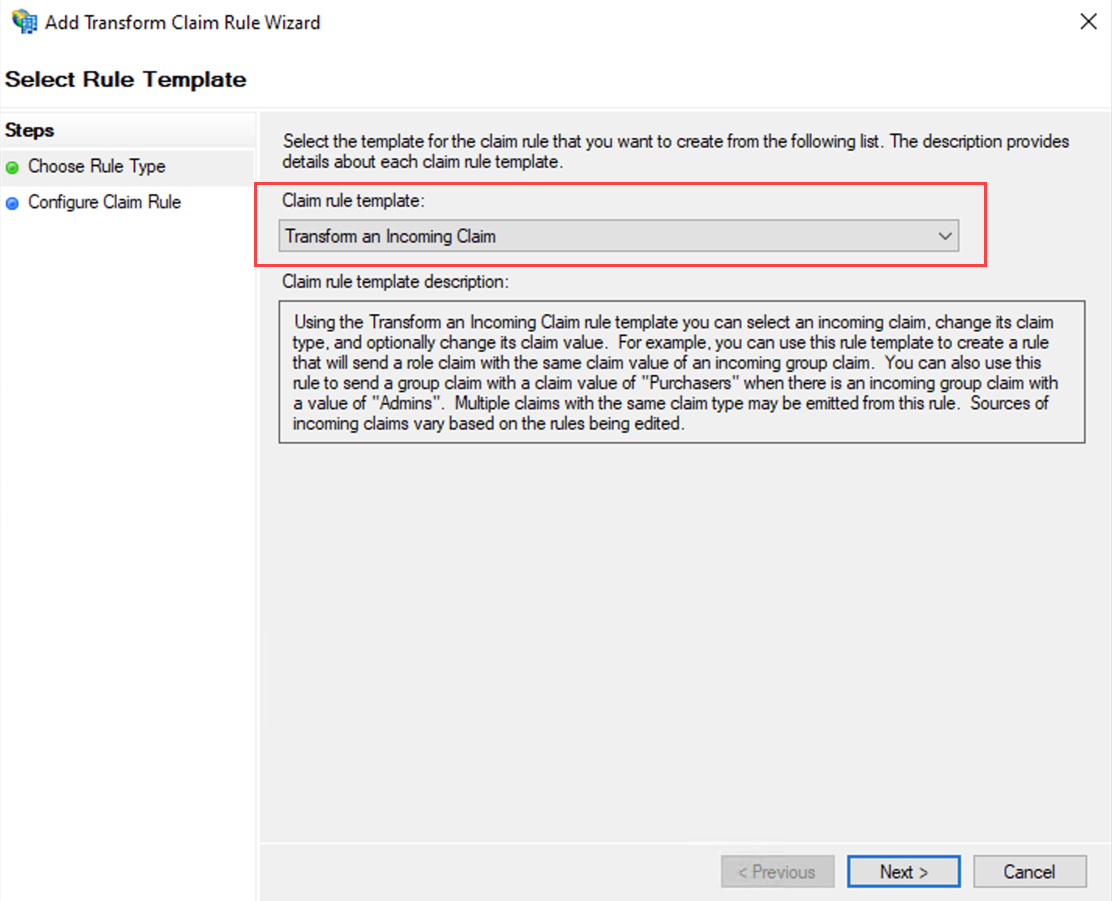
Select Rule Template
On the Select Rule Template page, from the Claim rule template list, select Transform an Incoming Claim, and then click Next.
-
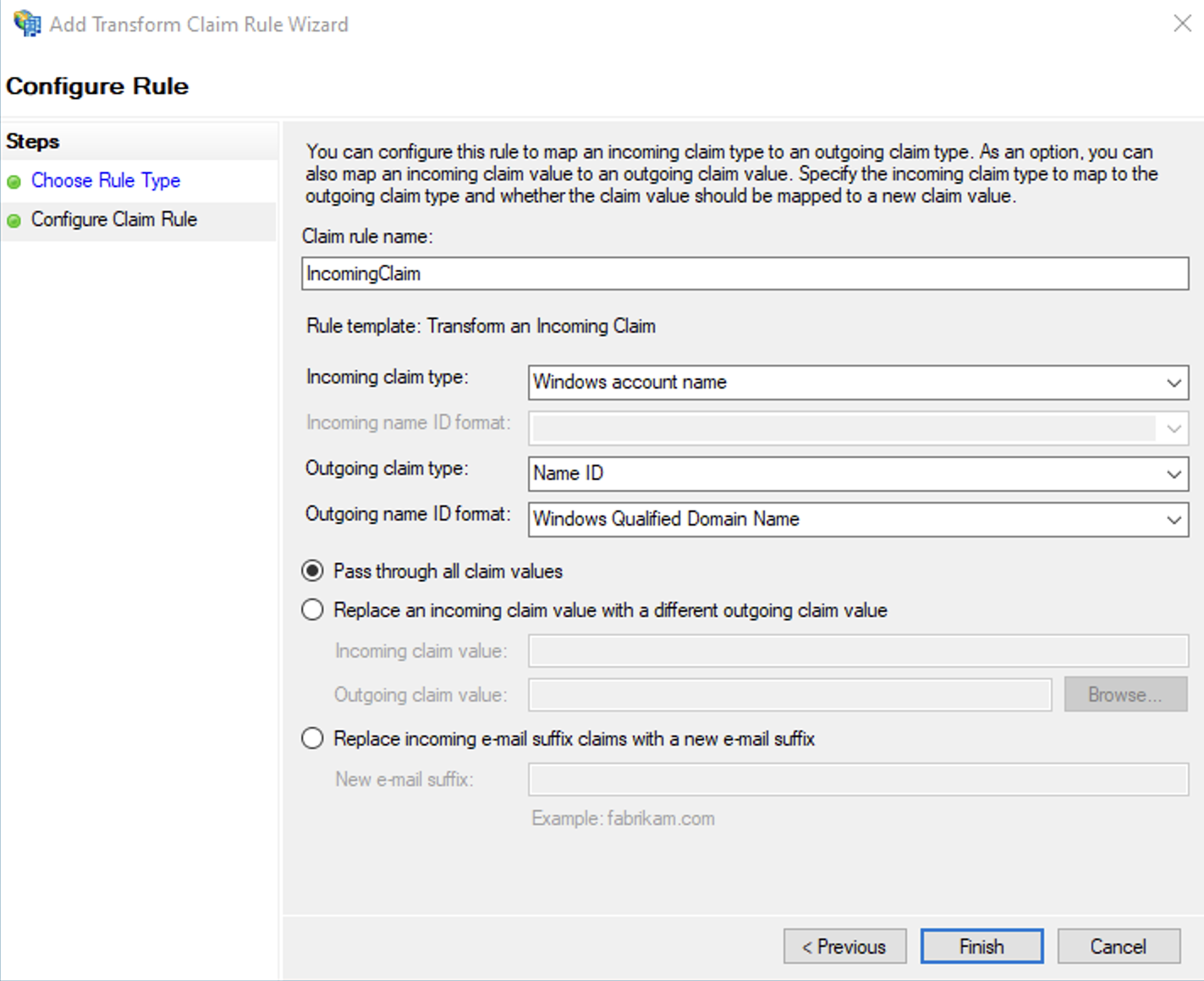
Configure Rule
On the Configure Rule page, do the following:
-
Under Claim rule name, type the display name for this rule. (for example, Incoming Claim).
-
In Incoming claim type, select Windows account name.
-
In Outgoing claim type, select Name ID.
-
In Outgoing name ID format, select Windows Qualified Domain Name.
-
Click Finish.
-
In the Edit Claim Rules dialog box, click OK to save the rule.
-
-
Create a Rule to Send LDAP Attributes as Claims
In the Edit Claim Issuance Policy dialog box, under Issuance Transform Rules, click Add Rule to start another rule wizard.
-
Select Rule Template
On the Select Rule Template page, choose Send LDAP Attributes as Claims and click Next.
-
Configure Rule
On the Configure Rule page, do the following:
-
Under Claim rule name, type the display name for this rule (for example, Outgoing Claim).
-
Select Active Directory as the Attribute Store.
-
Map LDAP attributes to the appropriate outgoing claim types. For example:
-
LDAP Attribute: E-mail-Addresses
-
Outgoing Claim Type: E-mail Address
-
-
Click Finish.
-
-
In the Edit Claim Rules dialog box, click OK to save all claim rules.
By following these steps, you have successfully created a Relying Party Trust in AD FS, enabling a secure federation relationship between your AD FS server and the Calibo Accelerate platform. This setup allows AD FS to handle authentication requests from Calibo Accelerate users. Note that the steps may vary slightly depending on the AD FS version you use, but the overall process remains the same.
After you successfully create the relying party trust for the Calibo Accelerate platform, return to the F24H Wizard screen and validate single sign-on.
| What's next? Platform Setup |