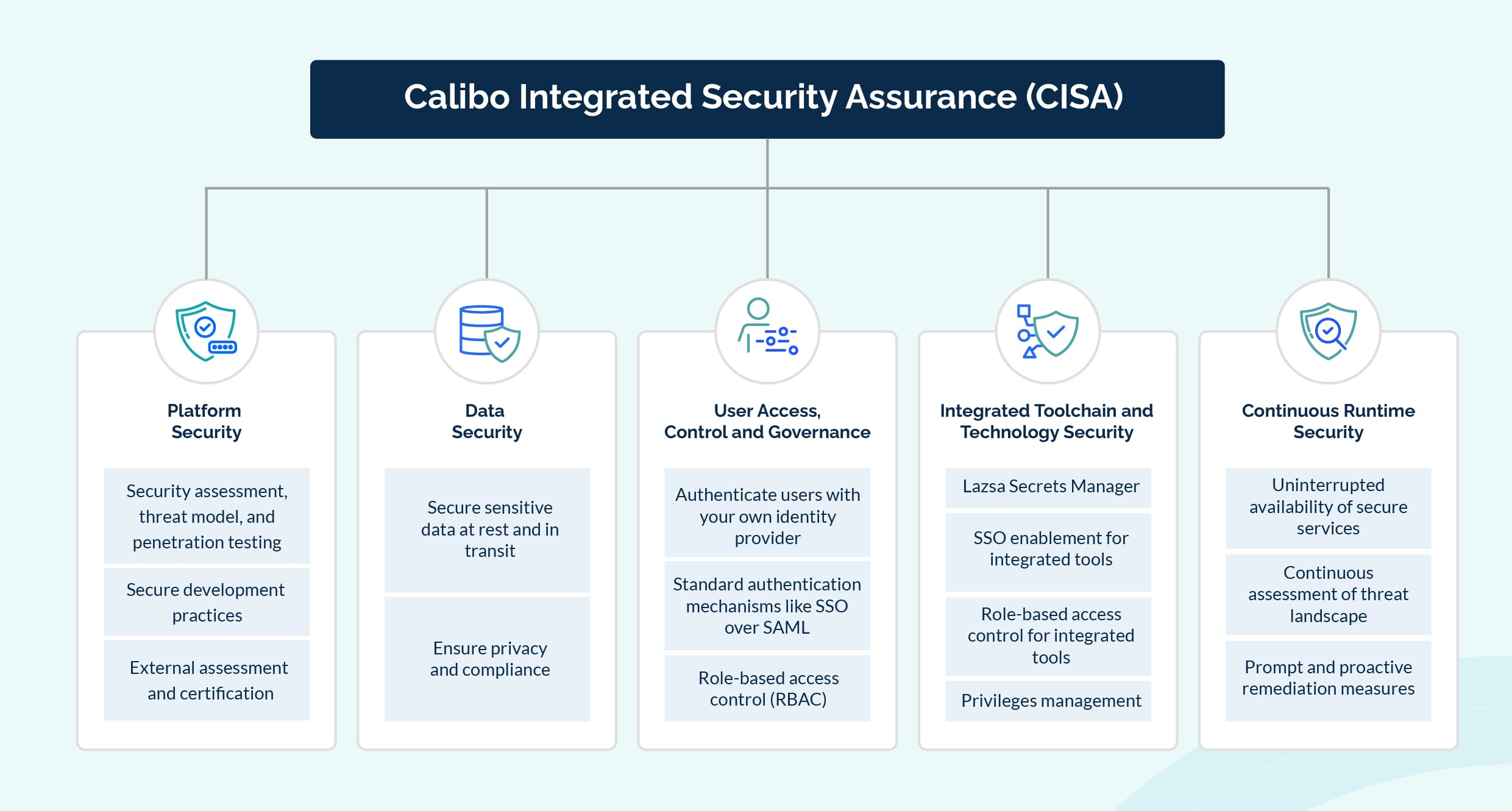
Components of CISA Framework
The Calibo Accelerate self-service platform is designed and developed by considering all your platform and data security requirements and by following the industry best practices. We boast a dedicated team of cyber security experts and we partner with leading cyber security agencies to certify the platform security. We have developed and enforced technological, physical, administrative, and logical security measures to continuously assess the overall security and compliance posture of the Calibo Accelerate platform.
CISA framework emphasizes on five major security areas in the Calibo Accelerate workflows and ensures comprehensive and continuous security and risk assessment.
Platform Security
Platform security is a comprehensive approach aimed at safeguarding the entire Calibo Accelerate ecosystem from potential threats. It encompasses several key practices and measures including the following:
-
STRIDE-Based Threat Model
Our security experts have developed a threat model based on STRIDE, which systematically evaluates and addresses potential security risks within the platform.
-
External Security Assessment
The Calibo Accelerate platform undergoes periodic security assessments, penetration testing, and certification conducted by leading external cyber security agencies. This ensures that our platform is rigorously evaluated and protected against emerging threats.
-
Continuous Issue Detection and Remediation
We have a continuous process in place to detect and remediate security issues throughout development, deployment, and configuration phases of a product. This proactive approach minimizes vulnerabilities.
-
Vulnerability Scanning
Regular scans and reviews are conducted on open-source components, source code, third-party tools, technologies, OS, and Docker images used in the Calibo Accelerate platform. This helps in promptly identifying and addressing newly-reported vulnerabilities.
-
Employee Training
Calibo invests in training programs for employees to enhance their cyber security awareness and to ensure the adoption of secure coding best practices. Security is not just a practice but embedded in our work culture.
-
Benchmark OS Images
We use benchmarked OS images for our infrastructure, ensuring that we start with a secure foundation.
-
Container Security
Industry-leading container security scanners are used in the Calibo Accelerate platform to thoroughly inspect nodes and containers running on the platform. This helps in identifying and mitigating container-related security risks.
-
Cloud Infrastructure Monitoring
Our cloud infrastructure is constantly monitored for security compliance. Periodic enforcement of security controls ensures that we meet industry standards.
-
Encryption Key Rotation
As a cryptographic best practice, encryption keys are rotated periodically in the Calibo Accelerate platform. Additionally, we utilize the latest secure encryption algorithms to ensure end-to-end data encryption.
Our commitment to platform security is comprehensive, proactive, and ingrained in every aspect of our operations. We prioritize the protection of our ecosystem and customer data to provide a secure and reliable environment for all our users.
Data Security
We ensure data security within the Calibo Accelerate platform with a comprehensive approach which includes the following practices:
-
Role-Based Access Control (RBAC)
Role-Based Access Control across the Calibo Accelerate platform ensures that users are authorized before gaining access to specific data and services. This means that individuals or teams are granted permissions based on their roles, ensuring that they can only interact with the data and functionalities relevant to their responsibilities. RBAC helps prevent unauthorized access and potential data breaches.
-
Calibo Accelerate Secrets Manager
To safeguard sensitive information such as tools credentials, API keys, tokens, and other secrets, a dedicated Secrets Manager is used in the Calibo Accelerate platform. This secure repository ensures that secrets are stored in an encrypted and protected environment. Unauthorized access to these secrets is rigorously controlled.
-
Security Protocol Adherence
The Calibo Accelerate platform follows stringent security protocols when handling data, both in storage and during transmission. This includes encryption, secure communication channels, and industry-standard practices to maintain the confidentiality and integrity of data.
-
Privacy Compliance
The Calibo Accelerate platform complies with the latest data protection laws, regulations, and best practices. This ensures that user data is handled with the utmost care and in accordance with legal requirements.
-
Isolation of Calibo Accelerate Services
As a proactive approach, Calibo Accelerate services are isolated from your valuable intellectual property (IP) and production workloads. This separation provides you with full control over your data, minimizing the risk of data compromise or leakage. Your data remains under your control, enhancing data security.
In summary, the data security strategy for the Calibo Accelerate platform is implemented proactively to protect your sensitive information. It encompasses role-based access control, dedicated secrets management, adherence to best practices, and compliance with data protection laws.
User Access, Control, and Governance
In this age of data-driven innovation and an ever-evolving threat landscape, ensuring that the right individuals have the right access to the right resources is important. The Calibo Accelerate platform empowers you to manage user access, enforce governance policies, and maintain control over your digital landscape by implementing the following:
-
Federated Authentication
The Calibo Accelerate platform employs federated authentication protocols such as SAML (Security Assertion Markup Language) and OpenID. These standards enable seamless and secure access to Calibo Accelerate services. They allow users to use their existing corporate Single Sign-On (SSO) credentials to sign in, simplifying the authentication process and ensuring compatibility with various Identity Providers (IdPs).
-
Integration with Corporate SSO
The Calibo Accelerate platform seamlessly integrates with corporate Single Sign-On solutions, including industry-standard IdPs like Microsoft Active Directory and Azure Active Directory. This integration streamlines user access management and ensures that the platform aligns with existing authentication infrastructure of your organization.
-
Multi-Factor Authentication (MFA)
To provide an extra layer of protection, the Calibo Accelerate platform supports multi-factor authentication. Users are required to provide multiple forms of verification, such as a password and an authentication token, enhancing security and reducing the risk of unauthorized access.
-
User Authorization with RBAC
The Calibo Accelerate platform employs Role-Based Access Control (RBAC) model for user authorization. This means that users are assigned specific roles, each with predefined permissions. Custom roles can also be created to grant fine-grained access to resources based on project requirements. RBAC ensures that users only have access to the functionalities and data necessary for their roles, minimizing the risk of data breaches.
-
Comprehensive Auditing
The Calibo Accelerate platform maintains detailed audit logs that record all user and system actions. These logs are essential for governance and control, providing visibility into who accessed the platform, what actions were performed, and when they occurred. This audit trail is valuable for compliance purposes and security monitoring.
-
Policy Templates
Policy templates allow you to define and enforce access restrictions at various levels. You can apply these policy templates to optimize and standardize the use of cloud infrastructure, resources, and tools.
Calibo's comprehensive approach to user access, control, and governance includes federated authentication, strong multi-factor authentication, RBAC for precise authorization, detailed auditing for transparency, and policy templates for fine-tuned access control. This ensures that your organization can manage and secure user access effectively while maintaining governance and compliance.
Integrated Toolchain and Technology Security
-
Credential Handling
Credentials for integrated tools and technologies are not stored in the Calibo Accelerate platform unless explicitly specified by the user. This minimizes the exposure of sensitive information.
-
Third-Party Secrets Store Integration
The Calibo Accelerate platform seamlessly integrates with your desired secrets store solutions like AWS Secrets Manager, Azure Key Vault, and others. This means that credentials for integrated tools and technologies are retrieved directly from these secure stores.
-
Calibo Accelerate Orchestrator Agent
This service is deployed within your network to establish a secure connection between your tools and the Calibo Accelerate platform. Credentials are retrieved programmatically from your secrets management tool and are never shared with the platform.
See Calibo Accelerate Orchestrator Agent.
-
Single Sign-On (SSO) and Role-Based Access Control
Integrated tools and technologies are accessed through SSO, enhancing authentication security. Moreover, role-based access control (RBAC) is applied to ensure that users have access only to those functionalities and data that they are authorized to use.
-
User Privilege Management
The Calibo Accelerate platform provides a granular approach to user privilege management. This allows administrators to finely delegate access rights to both users and applications within the platform, enhancing security and control over access to integrated tools and technologies.
See Connecting to Tools from the Calibo Accelerate platform.
Continuous Runtime Security
To ensure protecting your applications and data throughout their life cycle, the Calibo Accelerate platform follows a proactive continuous runtime security strategy. Here's how it's achieved:
-
Continuous Monitoring
Calibo Accelerate services are continuously monitored for both their health and security. Any potential issues or security threats are promptly detected, allowing for immediate action.
-
Uninterrupted Availability
The Calibo Accelerate platform prioritizes uninterrupted availability of services. This is achieved through clustering, auto-scaling, and disaster management mechanisms. Even during unexpected events, such as server failures, services remain accessible and performant.
-
Security Tools
Calibo Accelerate uses industry-leading security tools that continuously monitor both the infrastructure and application layers. These tools identify security vulnerabilities and potential threats. Upon detection, proactive measures are taken to remediate these issues, preventing security breaches.
-
Minimal Downtime
During the remediation process, Calibo Accelerate aims to keep downtime to a minimum. This ensures that Calibo Accelerate services remain accessible, even when security updates or patches are being applied.
-
Data Management
Established practices for periodic data backup, recovery, and management are followed for the Calibo Accelerate platform. This ensures that your data is safeguarded and can be restored in case of data loss or corruption.
Overall, this continuous runtime security strategy proactively safeguards your applications and data, ensuring they remain secure, available, and performant at all times.
| What's next? Connecting to Tools from the Calibo Accelerate platform |