Prerequisites to Install Calibo Accelerate Orchestrator Agent on Amazon EKS Cluster by Using mTLS
To install a Calibo Accelerate Orchestrator Agent on an Amazon EKS cluster by using mTLS, complete the following prerequisites:
A dedicated EKS cluster is required to deploy Calibo Accelerate Orchestrator Agent. Consider the following minimum requirements for compute resources as you configure the Kubernetes nodes in the cluster:
EKS Cluster Requirements
-
EKS version 1.24 or later
-
Minimum 2 nodes (Minimum 8GiB RAM and 2vCPU per node)
-
Deploy the EKS cluster in the same region where the Calibo Accelerate platform is deployed. For any queries, contact Calibo Technical Support Team.
-
Create EKS cluster IAM role and Amazon EKS node IAM role as per the AWS guidelines.
Install NGINX Ingress Controller with Network Load Balancer (NLB) in the EKS cluster that you created in prerequisite 1. We recommend using an internal NLB, which ensures that the Ingress Controller is accessible only within the cluster's internal network, enhancing security.
NGINX Ingress Controller Requirements
-
Version 1.3.0 or later
For information about how to install the Ingress-Nginx Controller, see Ingress-Nginx Controller Installation Guide.
-
Configure AWS Secrets Manager in the same AWS account as the Amazon EKS Cluster used for deploying the Calibo Accelerate Orchestrator Agent.
-
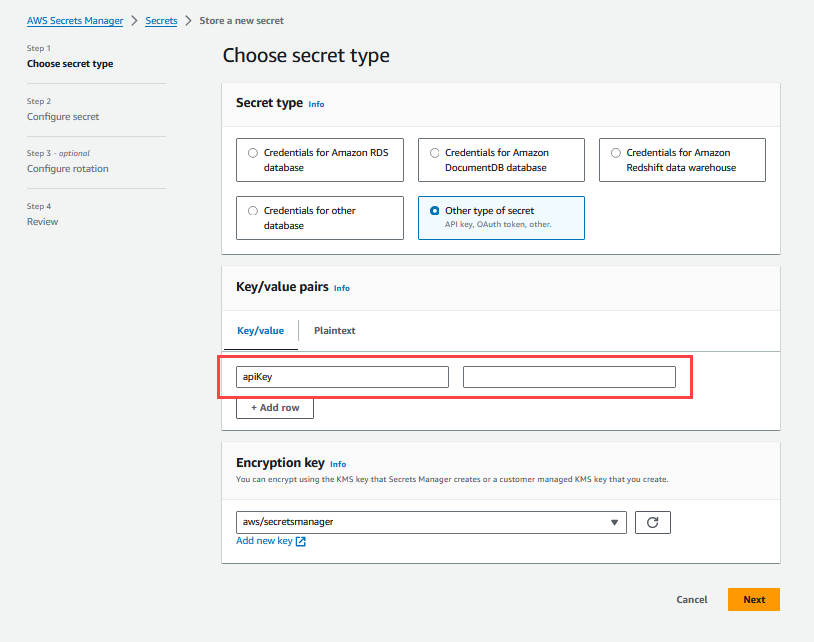
Open the Secrets Manager console at https://console.aws.amazon.com/secretsmanager/.
-
Click Store a new secret.
-
For Secret type, select Other type of secret.
-
In Key/value pairs, add the following key with its value as an empty string.
Key apiKey
Note:
This is a predefined secret used by the Calibo Accelerate Orchestrator Agent. Do not change the key name.Value <empty string>
-
On the next page, provide the secret name. For more information, refer to AWS documentation.
Calibo Accelerate Orchestrator Agent uses this placeholder secret to store its API key. This key is used to authenticate the API requests sent from the Calibo Accelerate platform.
-
Create an IAM policy to allow the Amazon EKS node to resolve secrets from AWS Secrets Manager and to update the API token secret (
apiKey) that you created in the earlier section.Refer to the following sample IAM policy:
Sample IAM PolicyWhile editing this sample IAM policy, replace the following placeholder values with your actual values. This sample policy contains minimal permissions which must not be altered.
Placeholder Value Expected Value <AWS Region>Replace this with your AWS region name. <Account ID>Replace this with your AWS account ID. <Secret Name>Replace this with the name of the tool's secret that you want Calibo Accelerate Orchestrator Agent to resolve. For each tool's secret, add a separate entry in the policy.
"Resource": [
"arn:aws:secretsmanager:<AWS Region>:<Account ID>:secret:<Secret Name 1>",
"arn:aws:secretsmanager:<AWS Region>:<Account ID>:secret:<Secret Name 2>",
"arn:aws:secretsmanager:<AWS Region>:<Account ID>:secret:<Secret Name 3>"<secret-name-for-api-token>Replace this with the name of the placeholder secret that you configured in prerequisite 3.
"Resource": "arn:aws:secretsmanager:<AWS Region>:<Account ID>:secret:<secret-name-for-api-token>"
Note:
The sample policy allows the Amazon EKS node on which the Calibo Accelerate Orchestrator Agent runs to update the value of this secret during key rotation.
Copy{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"secretsmanager:GetSecretValue",
"kms:Decrypt",
"secretsmanager:DescribeSecret"
],
"Resource": [
"arn:aws:secretsmanager:<AWS Region>:<Account ID>:secret:<Secret Name 1>",
"arn:aws:secretsmanager:<AWS Region>:<Account ID>:secret:<Secret Name 2>",
"arn:aws:secretsmanager:<AWS Region>:<Account ID>:secret:<Secret Name 3>"
]
},
{
"Effect": "Allow",
"Action": "secretsmanager:ListSecrets",
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "secretsmanager:UpdateSecret",
"Resource": "arn:aws:secretsmanager:<AWS Region>:<Account ID>:secret:<secret-name-for-api-token>"
}
]
} -
Attach this IAM policy to the Amazon EKS node IAM role that you have created while setting up your Amazon EKS cluster.
Allow inbound and outbound connectivity on port 443 to the Amazon EKS cluster on which you deploy the Calibo Accelerate Orchestrator Agent. Make sure that the following services are accessible from your EKS cluster:
-
Docker Hub
Ensure access to Docker Hub. This connectivity is required to download the Orchestrator Agent images from the Docker Hub. -
Amazon S3
Ensure connectivity to Amazon S3 to download Calibo Accelerate Orchestrator Agent Helm charts. -
Calibo Accelerate platform
Ensure the Calibo Accelerate platform is accessible from your EKS cluster. This connectivity is required to establish a secure connection between the Orchestrator agent and the Calibo Accelerate platform.
The following commands help you generate a self-signed Certificate Authority (CA) certificate, server certificate, and client certificate. You can also use your trusted root CA to generate these certificates.
-
Create a CA certificate by running the following command in your command line interface. Replace
Test Cert Authoritywith the name of your trusted certificate authority. The-daysparameter indicates the validity period of the certificate. By default, it is set to 365. You can modify this value. After the specified period, the certificate will expire and you must regenerate the self-signed CA certificate.Copyopenssl req -x509 -sha256 -newkey rsa:4096 -keyout ca.key -out ca.crt -days 365 -nodes -subj "/CN=Test Cert Authority" -
Create a server certificate for your domain by using the CA certificate that you created in step 1. To create the server certificate, run the following command in your command-line interface. Replace
<your_domain_name>with your domain name. The-daysparameter indicates the validity period of the certificate. By default, it is set to 365. You can modify this value. After the specified period, the server certificate will expire and you must regenerate it.Copyopenssl req -new -newkey rsa:4096 -keyout server.key -out server.csr -nodes -subj "/CN= <your_domain_name>" && openssl x509 -req -sha256 -days 365 -in server.csr -CA ca.crt -CAkey ca.key -set_serial 01 -out server.crt -
Create a client certificate by using the CA certificate that you created in step 1. To create a client certificate, run the following command in your command line interface. The
-daysparameter indicates the validity period of the certificate. By default, it is set to 365. You can modify this value. After the specified period, the certificate will expire and you must regenerate the certificate and upload it to the Calibo Accelerate platform by editing the agent details.Copyopenssl req -new -newkey rsa:4096 -keyout client.key -out client.csr -nodes -subj "/CN=Lazsa" && openssl x509 -req -sha256 -days 365 -in client.csr -CA ca.crt -CAkey ca.key -set_serial 02 -out client.crt -
Convert the client certificate to PKCS#12 format by running the following command. Remember the password that you add to create the certificate in PKCS#12 format. You must provide this password when you upload the client certificate during agent installation.
Copyopenssl pkcs12 -export -out client.p12 -inkey client.key -in client.crt
| What's next? Steps to Install Calibo Accelerate Orchestrator Agent in Amazon EKS Cluster by Using mTLS |