Configure Single Sign-on with SAML
Use this screen to connect your Calibo Accelerate tenant to any SAML-compliant Identity Provider (IdP)—such as Okta, or Ping Identity—so users can sign in with their enterprise credentials. On this screen, you’ll configure the SAML details required to establish a trust relationship between your Identity Provider (IdP) and Calibo Accelerate.
Before You Start (Prerequisites)
Before setting up SAML-based Single Sign-on (SSO) in Calibo Accelerate, make sure your organization’s identity and access management setup meets the following prerequisites.
-
Have Administrative Access to Your Identity Provider (IdP)
You must have administrator privileges in your organization’s Identity Provider (IdP) to create or modify SAML applications.
This allows you to:
-
Register Calibo Accelerate as a new application (service provider) in your IdP.
-
Configure important parameters such as Assertion Consumer Service (ACS) URL, Entity ID, and attribute mappings.
-
Generate and download the X.509 signing certificate used to sign SAML assertions.
-
Access the metadata XML file or metadata URL, which is required to establish the trust relationship between Calibo and your IdP.
-
-
Decide the Email Domain to Associate with Your Tenant
Each tenant in Calibo Accelerate is tied to an email domain (for example, mycompany.com).
When you configure SAML-based SSO in Calibo Accelerate, you must specify this domain in the F24H wizard. Only users whose email addresses match this domain can be added and sign in to the tenant through SSO.
For example, if you specify mycompany.com as your domain, a user with ajones@mycompany.com can be added, but a user with ajones@partner.org cannot be added.
-
Identify and Add Users in the F24H Wizard
The users you add for SAML configuration in the F24H Wizard must already exist in your IdP and have valid email addresses on the configured domain.

Note:
Calibo currently does not support automatic user synchronization (user import) for SAML. You need to add users manually and choose administrators.
-
Prepare Attribute Mapping Details
SAML authentication relies on user attributes (also known as “claims”) exchanged between your IdP and Calibo Accelerate. Before you configure SAML settings in Calibo Accelerate, decide which attributes will be passed in the SAML response.
At minimum, Calibo requires:
email → to identify and log in the user.
It is strongly recommended to also include:
-
firstName → user’s given name.
-
lastName → user’s surname or family name.
-
-
Plan for Certificate Management and Rotation
Have access to your IdP’s signing certificate or metadata file.
Every SAML integration uses an X.509 certificate to sign authentication responses (assertions) from the IdP. Certificates have an expiration date, and if they expire or change without reconfiguration, all SSO logins will fail.
Make sure you know the certificate’s validity period and have a process in place for future rotation.
After all the above prerequisites are in place, you can proceed with configuring SAML in Calibo Accelerate using one of the available methods — Manual Configuration, Import from URL, or Import from Metadata File.
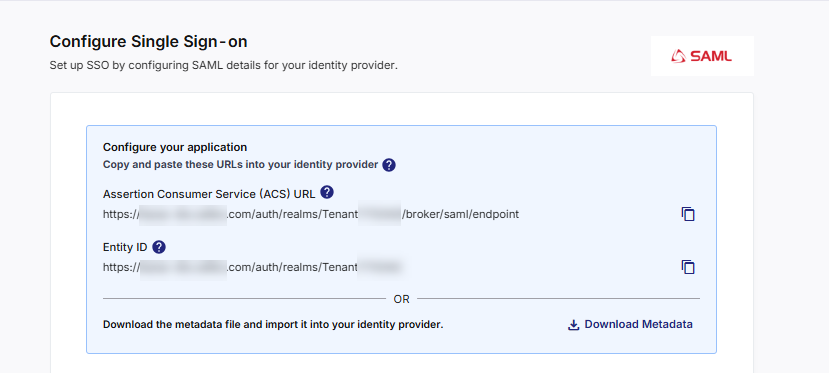
Configuring SAML Details in Calibo Accelerate
Calibo acts as the Service Provider (SP) and provides the required parameters for you to use while creating or updating the SAML application in your IdP. The screen displays the following values:
-
Assertion Consumer Service (ACS) URL
The endpoint in Calibo Accelerate that receives authentication responses (SAML assertions) from your IdP after a user successfully signs in.
Example:
https://accelerate-dis.calibo.com/auth/realms/<TenantID>/broker/saml/endpoint
-
Entity ID
A unique identifier for Calibo Accelerate as the Service Provider. It tells the IdP which application is requesting authentication.
Example:
https://accelerate-dis.calibo.com/auth/realms/<TenantID>
You can either copy these URLs and paste them into your IdP configuration manually or download the metadata file and import it directly into your IdP to simplify setup.

Tip:
Using the metadata file is the recommended approach as it reduces manual entry errors and ensures consistency during certificate rotation.
Selecting a Configuration Method to Provide SAML Details
Calibo Accelerate offers three ways to configure SAML details, depending on how your IdP manages metadata and endpoints.
Choose one of the following configuration methods:
Option A — Configure Manually
Select this method if you prefer to enter the required IdP details directly into Calibo Accelerate. Enter the following details:
-
Domain – The email domain (for example, mycompany.com). Only users whose email addresses match this domain can be added to the platform.
-
Single Sign-on (SSO) URL – The endpoint in your IdP where users are redirected for authentication.
-
Single Logout (SLO) URL (optional) – The endpoint in your IdP for handling logout requests.
-
Signing Certificate – The IdP’s X.509 certificate used to sign SAML assertions. If your IdP rotates certificates periodically, plan to update this certificate in Calibo accordingly.
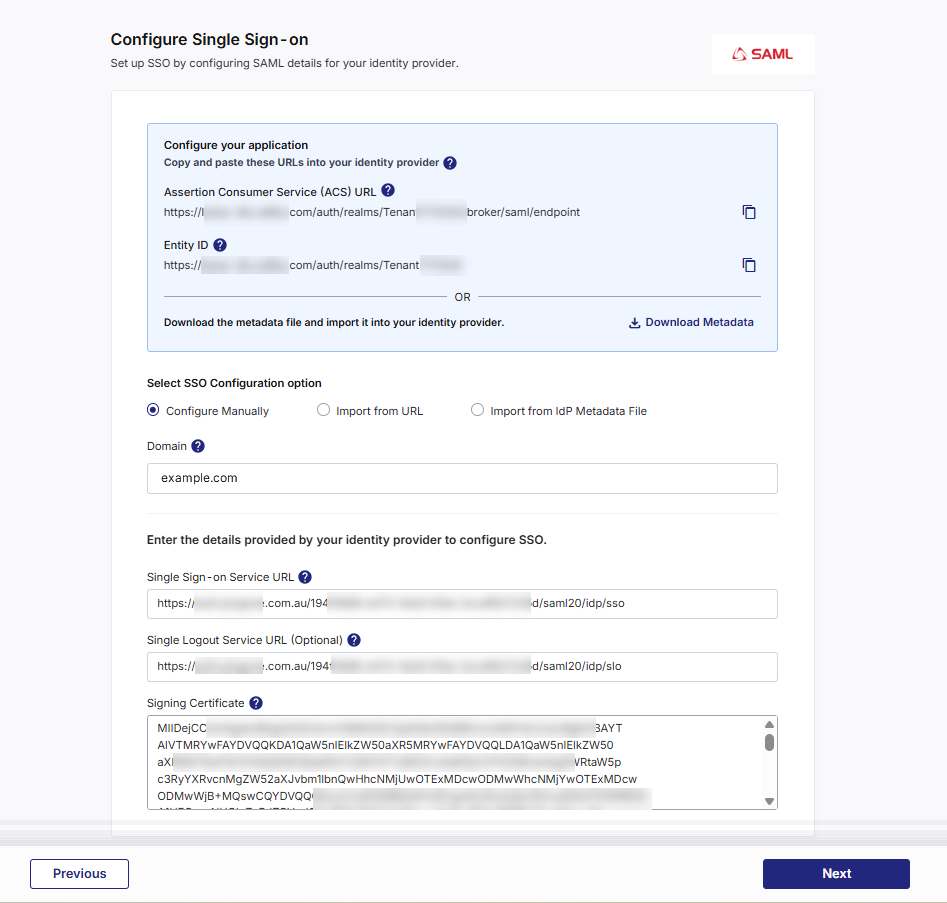
Use this method when your IdP doesn’t expose a metadata file or URL or when your security policy requires manual configuration.
Option B — Import from URL
Select this method if your IdP provides a metadata URL that hosts the configuration details required for SSO integration.
-
Enter the following details:
-
Domain – The email domain (for example, mycompany.com). Only users whose email addresses match this domain can be added to the platform.
-
IdP Metadata URL – The URL where your IdP hosts its SAML metadata XML. Calibo will automatically import all key information such as SSO URL, certificate, issuer, and supported bindings.
-
-
Click Import.
Calibo Accelerate connects to the provided URL and automatically imports the following details from your IdP metadata:
-
Single Sign-on (SSO) URL – The endpoint where users are redirected for authentication.
-
Single Logout (SLO) URL – The endpoint used for logout requests.
-
X.509 Certificate – The public certificate that your IdP uses to sign SAML assertions.
-
This method minimizes manual effort and automatically reflects certificate or endpoint updates from your IdP.
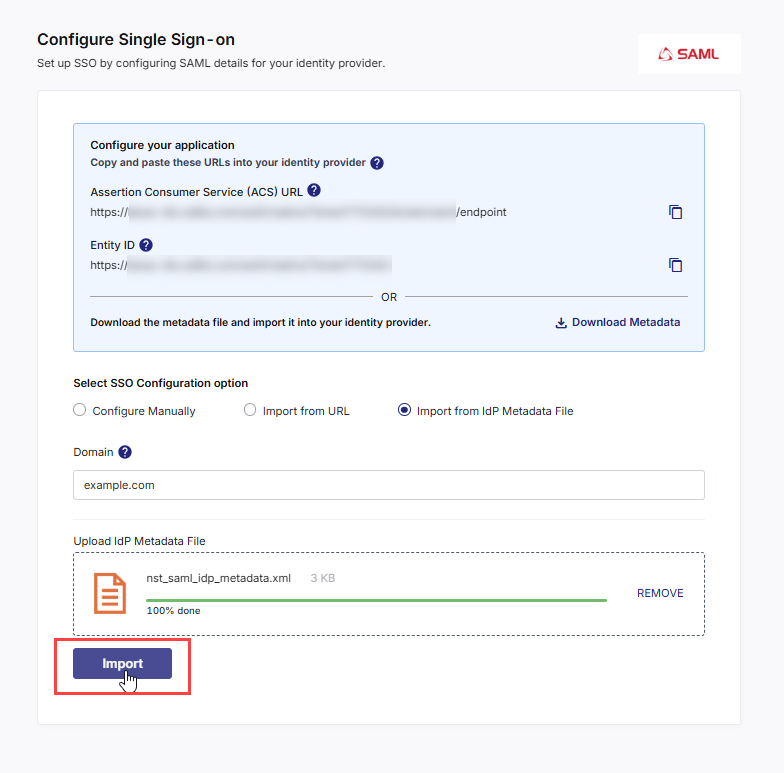
Option C — Import from Metadata File
Select this method if your IdP allows you to export its SAML metadata file (usually an .xml file) that contains all configuration details.
Do the following:
-
Enter the Domain
Specify your organization’s email domain (for example, mycompany.com). Only users whose email addresses match this domain can be added to the platform.
-
Upload IdP Metadata File
Upload the metadata XML file exported from your IdP. Do one of the following:
-
Drag and drop your metadata XML file into the drop zone.
-
Click Browse this computer to select the metadata XML file manually.
-
-
Click Import
After the file is uploaded, click Import.
-
Calibo Accelerate reads and parses the XML file to automatically import the following configuration details:
-
Single Sign-on (SSO) URL – The endpoint for user authentication requests.
-
Single Logout (SLO) URL – The endpoint for logout requests (if provided by your IdP).
-
X.509 Certificate – The public certificate used by your IdP to sign authentication assertions.

Tip:
-
Ensure the metadata XML file is generated directly from your IdP without manual edits.
-
Whenever your IdP rotates certificates or updates SSO endpoints, download the new metadata XML and re-import it here to maintain SSO continuity.
-
This method is recommended for restricted or on-premise environments where direct metadata URLs are not accessible.
Tip:
Regardless of which method you choose, always verify that the IdP configuration includes:
-
The correct ACS URL and Entity ID as provided by Calibo.
-
Signed Assertions enabled in your IdP.
-
email as the NameID format or attribute for consistent user identification.
Click Previous to return to the previous screen.
Click Next to proceed with adding users to the tenant.
Adding Users and Assigning Administrators in Calibo Accelerate
After you’ve configured your SAML connection details, the next step in the F24H Wizard is to add users who will access the Calibo Accelerate platform under this tenant.
Unlike integrations with Microsoft AD or Azure AD, SAML-based tenants currently do not support automatic user synchronization. This means that you need to manually add users in this step before assigning administrative roles.
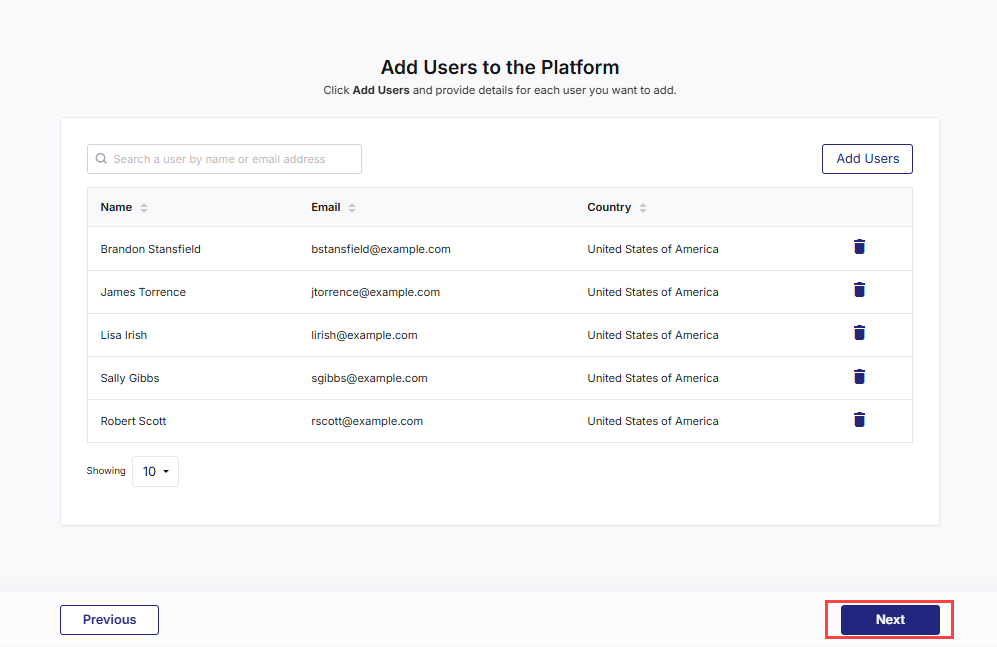
Adding Users Manually
-
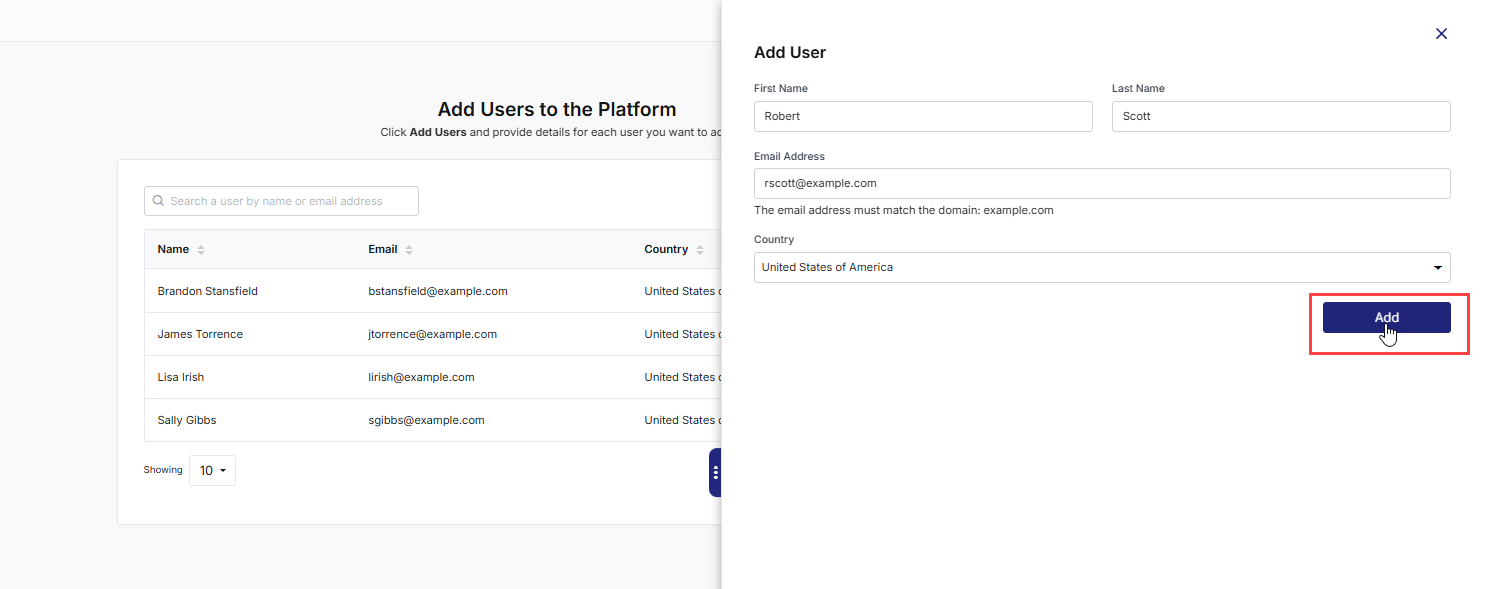
Click Add Users.
-
In the side drawer, provide the following details for each user:
-
First Name: Enter the first name.
-
Last Name: Enter the last name.
-
Email Address – This must belong to the domain you configured during SSO setup (for example, @mycompany.com).
-
Country: Select a country from the dropdown list.
To add all desired users, repeat the above steps. Include all individuals who need immediate access to the Calibo Accelerate tenant — such as product owners, developers, DevOps engineers, or administrators.

Note:
Since user synchronization is not yet available for SAML configurations, any new users you want to onboard later must also be manually added through the Users, Roles, Teams, and Organization Hierarchy section of the platform.
-
-
After you add all desired users, click Next to select tenant administrators.
Selecting Administrators
-
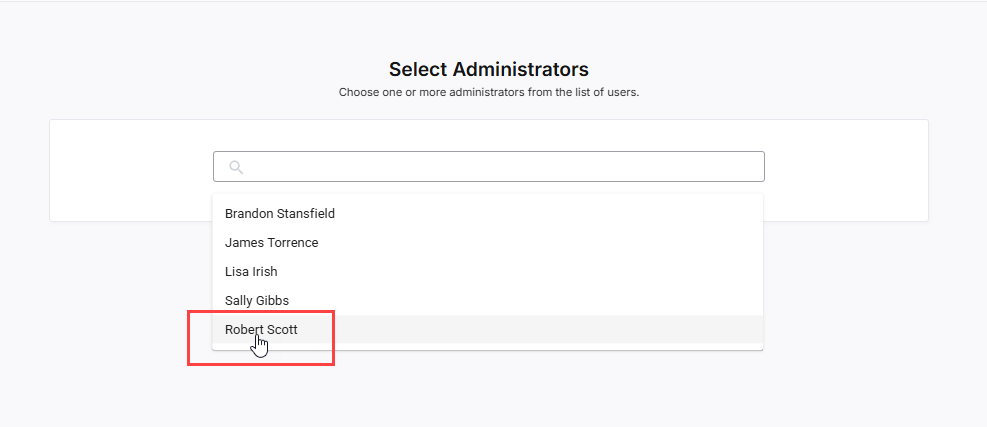
On the Select Administrators screen, click inside the search bar.
-
Start typing the name of a user you added on the previous screen.
As you type, a dropdown list appears showing matching user names.
-
Click the user’s name from the search results to select them as an administrator.
-
Repeat the process to add multiple administrators, if required. You can assign one or more users as administrators based on your organization’s governance model.
-
After you add administrators, click Next to review the list of platform users and administrators.
Reviewing Platform Users
The Platform Users screen displays the list of all the administrators and users you chose to add to the Calibo Accelerate platform in the previous steps. The details such as each user's name, email address, and country are displayed. The Status column indicates whether the user was successfully added or if there was an issue. In case of failure, review the error messages and take the necessary action.

Click Next to proceed.
| What's next?Platform Setup |